A DIGITAL EYE - Part 2 The Dark Side of Webcam Surveillance
In this blog post, we are discussing the negatives of webcam surveillance


Whereas webcams have revolutionized security, communications, and home working, there is a darker side. These devices have the potential to be used by hackers, cybercrooks, and even intelligence agencies to trespass on privacy, carry out extortion, and serve to drive underground economies. A vast, untraceable infrastructure lurks wherein cybercrooks sell stolen webcam feeds, blackmail targets, and transform ordinary cameras into surveillance weapons.
Blackmail & Sextortion
Among the most chilling webcam crimes is sextortion—the hacking of victims secretly through their own devices to extort money, nude videos, or other concessions in exchange for not distributing the videos. The crime strikes young people primarily, but everybody is vulnerable to it. Cases involving celebrities have revealed how professionals and ordinary folks have been similarly victimized.
Most attackers take control of a victim's webcam using Remote Access Trojans (RATs). These, once installed—usually by way of phishing emails, suspicious software downloads, or corrupt attachments—enable hackers total command of the camera, typically without activating the indicator light. Victims can be secretly recorded during intimate moments and be unaware of the surveillance. Some hackers are not so eager to act in the moment and prefer to archive recordings for several months or years before making their extortion plays.
Voyeuristic Forums & The Market for Hacked Webcams
Under the surface web is a darker reality—hidden forums where cyber-thieves and voyeurs sell hacked webcam streams. Some sites even broadcast hijacked security cameras, baby monitors, and home webcams in real time. Usually, they are open to use because users do not bother to reset default passwords, and thus they are easily discovered.
Whereas some of these forums have been shut down, others remain popular. Hackers offer webcam access for a fee, ranging from private home video feeds to surveillance of boardrooms. Some are chillingly designed to allow paying subscribers to browse various sites or victim profiles.
RATs & the Tools of Webcam Hijackers
Malware that can hijack webcams is readily available on the dark web. Software such as BlackShades, DarkComet, and njRAT have been employed to hijack millions of webcams, allowing hackers to have complete control over a victim's computer, including access to their files, microphone, and camera. In certain dark market communities, employing these tools is considered entertainment—known as "ratting" or "slaving" victims.
Even novice cybercrooks can purchase these tools for $10–$50. There are several hacking forums that offer tutorials on how to use them, which makes it simpler for people with even basic technical expertise to take advantage of unsuspecting victims.
Government & Corporate Surveillance: No One Is Safe

Webcam exploitation is not only reserved for criminals—governments and companies have been caught secretly accessing cameras as well. In 2014, leaked documents exposed that the NSA and GCHQ had harvested millions of photos from Yahoo webcams, including intimate material from unwitting users. Likewise, certain firms have come under fire for spying on their workers using installed webcams, often unknown to them. Boardroom cameras have been broken into to pilfer business secrets, and so even businesspeople need to be careful about webcam exploits.
How Webcams Are Used Against Us: The Tools and Tactics
The methods used in webcam exploitation range as far from high-tech malware infection to social engineering and even outright user ignorance. What follows outlines the primary methods hackers and cyber crooks use to take control of webcams for nefarious purposes.
1. Remote Access Trojans (RATs): Malware That Grants Full Control
One of the most harmful and most popular webcam hijack methods is by using Remote Access Trojans, or RATs. A RAT is a type of malware that is specifically created to give hackers remote access to gain complete control over a victim's computer, all the way up to being capable of viewing their files, keystrokes, and webcams.
How RATs Work
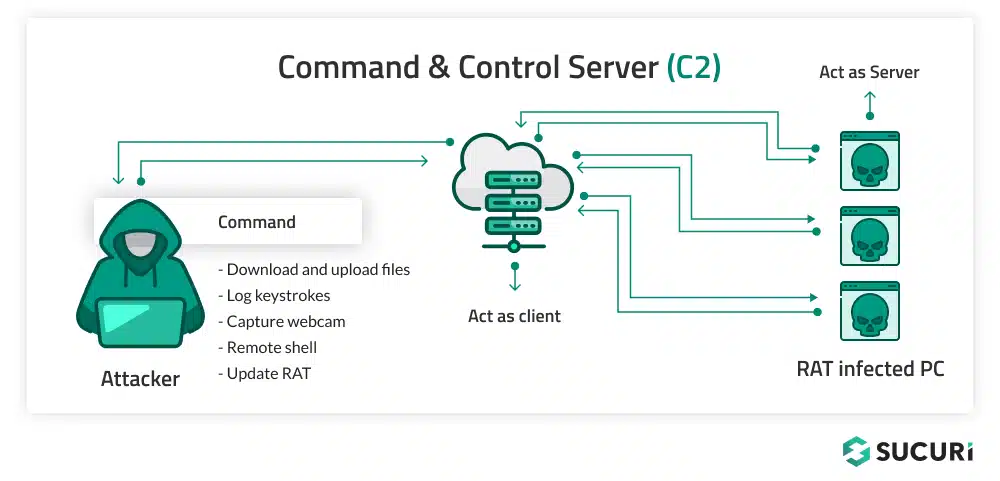
RATs are frequently disguised as genuine files and, for this purpose, are spread through multiple attack vectors, such as:
• Phishing Emails: Infected emails or attachments download malware.
• Fake Update Software: Criminals trick people into downloading RAT software by disguising it as system updates or essential drivers.
• Malicious Websites & Ads: Opening infected ads or visiting compromised websites can download a RAT.
• USB Infection: Certain RATS spread themselves using USB drives, quietly being installed once in the USB devices.
Silent Webcam Hijacking
After installation, a RAT can bypass webcam lights, enabling hackers to observe and record without the victim's awareness. Many advanced RATs, like BlackShades and DarkComet, include built-in features to disable webcam indicator LEDs, ensuring stealth surveillance.
Notable Cases
BlackShades RAT (2014):

Priced at as low as $40, this malware infected thousands of computers so hackers could remotely trigger webcams.
DarkComet RAT:

DarkComet RAT, one of the most widely distributed Trojans ever, has been used for cyber-spying in targeted surveillance attacks.
2. Phishing Attacks: Tricking Victims Into Installing Webcam Malware
Phishing remains one of the most efficient methods for deceiving victims to unknowingly download malware that enables webcam access. Unlike RATs that are dependent on software installation, phishing relies on specific social engineering and capitalizes on the psychological vulnerabilities of humans instead of systemic ones.
Types of Phishing Attacks Used for Webcam Exploitation
Email Phishing: Spoofed emails from trusted parties (banks, social media platforms, or IT support) prompt users to click suspicious links or download attached malware.
Tech Support Scams: Victims are emailed fake messages stating their webcam has been hacked and asking them to download "security software"—which is malware.
Fake Video Chat Invitations: Other hackers send spoofed Zoom, Skype, or Google Meet invites. Opening the link downloads spyware that can take control of the webcam.
Social Media Phishing: Attackers impersonate friends or would-be romantic interests and send files that, when opened, install webcam-enabling malware.
Real-World Example: Sextortion Ransom
In 2019, a sextortion scam involved hackers emailing thousands of victims who claimed to have webcam recordings of them in compromising situations. They requested payment in Bitcoin, though they had no actual footage—but for many, the psychological threat was enough to induce payment.
Exploiting Weak Passwords & Default Settings
The majority of webcams, such as security cameras, baby cams, and smart home cameras, have their passwords too weak or their default settings unchanged and easily found online. The devices are easily found and accessed by hackers, most of the time without malware.
How Hackers Exploit Unsecured Webcams
- Shodan & Censys: The Search Engines for Hackers
- These tools scan the internet for unsecured webcams, allowing hackers to view live feeds with just a few clicks.
- Many users don’t realize their devices are publicly accessible due to factory settings.
- Credential Stuffing & Brute-Force Attacks
- Hackers use massive databases of leaked passwords to try thousands of login combinations in seconds.
- Many people reuse passwords, making it easy for cybercriminals to guess login details.
- Default Manufacturer Logins
- Some cameras come with hardcoded usernames and passwords (e.g., admin/admin), which users forget to change.
- Attackers often publish these default credentials on hacker forums, making it even easier to gain access.
Real-World Example: Insecam

Insecam was one of the infamous websites that were live streaming thousands of webcams from around the globe because of poor passwords and open configurations.
Government & Corporate Espionage: Unauthorized Webcam Access at a Large Scale
Webcam spying isn't only done by cybercriminals—governments and companies have also been caught secretly spying through webcams for bulk surveillance and corporate spying.
Government Surveillance & Webcam Exploitation

- Israeli Pegasus Spyware & Webcam Access:
- NSO Group’s Pegasus spyware has been used by governments worldwide to covertly access devices, including webcams and microphones.
- Journalists, activists, and politicians were among the targets, with reports confirming unauthorized surveillance through their devices.
- Pegasus exploits zero-day vulnerabilities, allowing complete control over a device without the user’s knowledge.
- China’s AI-Powered Surveillance:
- Reports have surfaced of state-sponsored efforts to remotely activate webcams for monitoring citizens, especially in high-security areas.
Corporate Espionage & Insider Threat

- Some businesses have been caught spying on employees through built-in webcams.
- Hackers targeting companies have infiltrated boardroom cameras to steal trade secrets.
Real-World Example: Pennsylvania privacy lawsuit

In 2010, a Pennsylvania school district was sued for secretly activating student laptops’ webcams to monitor them at home—without their knowledge or consent.
Dark Web Live Streams: The Black Market for Hacked Webcams
One of the most shocking abuses of webcams is their use in black markets of underground streaming.
How Hackers Make Money from Stolen Webcam Streams
- Voyeuristic Dark Web Forums:
- Hacked webcams are streamed in hidden forums where users can pay for access to private home cameras.
- Blackmail & Ransom Services:
- Criminals offer custom access to live feeds in exchange for cryptocurrency payments.
Major Dark Web Sites for Webcam Exploitation
- AlphaBay & DarkFox:
- Sold access to hacked security cameras and home webcams.
- Telegram & Discord Private Groups:
- Many hackers now trade live feeds in encrypted messaging apps rather than on traditional dark web sites.
Case: The 2018 Webcam Ransomware Campaign

A cybercriminal group hacked into thousands of webcams and offered the feed for sale to its paying subscribers. Victims were unaware that their private moments were being streamed in real-time.
The Dark Communities Behind Webcam Exploitation
Cybercriminals are not lone operators. They thrive in dark communities, where they share information, tools, and access to exploited webcams. These dark forums and encrypted messaging channels are marketplaces, learning centers, and networking platforms for hackers involved in cyber espionage, voyeurism, and extortion. Some of these communities are operating openly, but others are camouflaged on the dark web, encrypted messaging platforms, and invitation-only networks.
RaidForums
RaidForums was among the most notorious hacking forums, providing leaked databases, hacking resources, and webcam login credentials stolen from users. Though authorities closed it down in 2022, its successors still exist in private forums where hackers still exchange access to hijacked webcams.
Exploit.in & XSS.is: Russian Cybercrime Hubs

- Exploit.in and XSS.is are Russian-language hacking forums where cybercriminals discuss RATs (Remote Access Trojans), webcam hijacking methods, and exploits.
- These forums serve as learning centers where hackers share step-by-step guides on infiltrating webcams, often targeting poorly secured IP cameras.
Hackforums.net: A Training Ground for Cybercriminals
- Once a notorious hub for “script kiddies” (novice hackers), Hackforums.net became famous for distributing RATs and webcam-hacking tutorials.
- It was the breeding ground for BlackShades RAT, a malware that infected thousands of computers, allowing hackers to activate webcams without detection.
Telegram & Discord Private Channels
- Encrypted messaging apps like Telegram and Discord host private groups where hackers trade hacked webcam access.
- These groups are invitation-only, often requiring proof of hacking skills or cryptocurrency payments to join.
- Hackers share live streams from hacked webcams, sometimes in exchange for Bitcoin payments.
Dark Web Black Markets (AlphaBay, DarkFox, etc.)
- The dark web hosts black markets selling stolen webcam access, blackmail materials, and RAT software.
- AlphaBay (before it was taken down in 2017) had entire sections dedicated to selling access to compromised webcams.
- DarkFox is another active dark web market, selling custom spyware that can bypass modern security measures.
These networks prove to be strong, demonstrating webcam hacking is as much a business as voyeurism.
Real-World Cases of Webcam Exploitation
Webcam spying has been revealed to be conducted by cyberthieves and governments alike, fueling scandals worldwide. These are some of the most startling real-world cases of webcam hacking and their aftermaths.
1. NSA & GCHQ’s “Optic Nerve” Program (2014)

- Documents leaked by Edward Snowden in 2014 revealed that the NSA (United States) and GCHQ (UK) secretly collected webcam images from millions of Yahoo users.
- This surveillance program, called “Optic Nerve,” indiscriminately stored webcam snapshots every five minutes, including intimate and private footage of unsuspecting users.
- The revelations sparked global outrage, raising concerns about mass surveillance and privacy rights.
2. BlackShades Malware Scandal (2014)

- The BlackShades RAT (Remote Access Trojan) was sold for as little as $40, allowing cybercriminals to take over webcams remotely.
- The malware infected thousands of computers worldwide, leading to multiple cases of sextortion, spying, and data theft.
- In 2014, a massive crackdown led to 100 arrests across 19 countries, exposing how widespread webcam hacking had become.
3. Miss Teen USA Sextortion Case (2013)

- In one of the most chilling cases of webcam spying, a hacker took over the webcam of Cassidy Wolf, the winner of Miss Teen USA 2013.
- The hacker secretly recorded her and attempted to blackmail her for explicit content.
- After an FBI investigation, the attacker, Jared Abrahams, was arrested and sentenced to 18 months in prison.
4. Dark Web Live Streams of Hacked Webcams
- In several investigations, authorities have found websites where hackers broadcast live footage from compromised webcams.
- Some of these dark web communities allow viewers to request specific types of footage, including home cameras, hotel rooms, and even baby monitors.
5. Corporate Espionage Through Webcams

- Hackers and competing companies have used hijacked boardroom webcams to steal trade secrets and confidential information.
- In 2020, a major cybersecurity firm reported that hackers had infiltrated webcams of Fortune 500 companies, monitoring private business meetings and negotiations.
The Impact of Webcam Surveillance
The effects of webcam hacking extend far beyond mere invasion of privacy—they can result in psychological trauma, blackmail, disinformation, and enduring paranoia.
1. Loss of Privacy: You Never Know If Someone Is Watching
- Webcam hacking may make victims feel like they are always being watched.
- Most individuals never even know their webcam has been hacked until it's too late.
2. Sextortion & Blackmail: A Devastating Crime
- Stolen videos can be used as blackmail to extort victims.
- Threats to release intimate photos unless a ransom is paid are common.
- This has resulted in instances of depression, damage to reputation, and even suicides.
3. Misinformation & Manipulation: The Rise of Deepfake Exploitation
- Stolen video footage can be altered using deepfake technology, allowing cybercriminals to create false evidence.
- Attackers can fake compromising videos of victims and use them for extortion or spread misinformation.
4. Mental & Emotional Toll: The Psychological Impact
- Most victims experience long-term fearfulness and paranoia, fearing that their intimate moments have been observed and recorded.
- Even after securing their devices, victims often struggle to trust technology again.
How to Safeguard Your Webcam Against Hacking
While the threat of webcam hacking exists, there is a lot you can do to keep yourself safe. Here's what to do:
1. Physical Protection: Cover Your Webcam
- Block off unwanted access using a webcam shield or just plain tape.
- When not in use, unplug external webcams to prevent remote activation.
2. Software Security: Keep Your System Updated
- Set up anti-malware and firewall software protection to ward off RAT infections.
- Keep your operating system and webcam drivers updated to prevent loopholes.
- Run an antivirus program that can detect RATs and spyware.
3. Network Safety: Secure Your Wi-Fi and Passwords
- Change default passwords for your security cameras and Internet of Things (IoT) devices.
- Employ strong, distinctive passwords and implement two-factor authentication (2FA) where feasible.
- Turn off remote access to webcams unless needed.
4. Awareness & Vigilance: Think Before You Click
- Do not click on dodgy links or download unfamiliar files.
- Be cautious of unusual messages or emails that ask for webcam access.
- Restrict app permissions—don't give too much access to your camera or microphone.
5. Check Your Webcam Light & Activity
- If your webcam light switches on unexpectedly, investigate right away.
- Look out for unusual processes running on your system that could be accessing your camera.
Conclusion
The dark side of webcams serves as a stark reminder that something as simple as a piece of equipment designed for communication can also be used for monitoring, blackmail, and cybercrime. Be it hackers using RATs to observe victims or government surveillance of citizens, your webcam may not be secure.
Although compromised cameras have been used for unethical and illegal purposes, webcams have also served innumerable purposes in matters of security, justice, and global connectivity. They have helped in solving crimes, exposing wrongdoings, and even helping save lives.
REFERENCES
References
- The Guardian - Optic Nerve: Yahoo Webcam Images Intercepted
- Wikipedia - Blackshades
- IEEE - DarkComet RAT Study
- EFF - Sextortion Scam
- Slate - Insecam: Website Exposing Security Cameras
- Financial Times - WhatsApp vs NSO Pegasus Spyware
- NY Post - Corporate Espionage & Hidden Cameras
- CNN - Pennsylvania School Webcam Lawsuit
- Trend Micro - 2018 Webcam Ransomware Campaign
- Webz - XSS Forum & Cybercrime
- ABC News - Blackshades Malware Scandal
- BBC - Miss Teen USA Sextortion Case
- Fox Business - Fortune 500 Companies Espionage






















