Intelphreak - January 8, 2025
2024 Cybersecurity Recap, New Non-Social Engineering TTPs, Major Browser Extension Supply Chain Attack, Japan Airlines DDoS Attack, OpenAI Fined €15 Million, HHS Proposes Changes to HIPAA, Researchers Discover New Lazarus Group Malware Campaign, Chinese Nation-State Actors Breach US Treasury Data

Precedence: Routine
BLUF: 2024 Cybersecurity Recap, New TTPs: "Laying Off Trusted Sites, WDAC EDR Bypass, Malicious npm Packages, and New KYC Bypasses", 2.6 Million Users Exposed in Major Web-Browser Supply Chain Attack, Japan Airlines Faces DDoS Attack, Italy Fines OpenAI €15 Million For Data Privacy Violations, HHS Proposes Changes to Strengthen HIPAA Security Rule, Researchers Discover New Lazarus Group Malware Campaign Targeting Nuclear Professionals, Chinese Nation-State Actors Breach US Treasury via Cybersecurity Vendor
BEGIN TEARLINE
[Research] A Cybersecurity Recap of 2024, with Insights for the Future
The cybersecurity field is both incredibly dynamic and dramatic, with attackers and defenders constantly in a game of cat-and-mouse with ever-evolving technology. Even in light of this fact, however, this was an exceedingly chaotic and groundbreaking year in the cyber realm! This year saw nonstop compromise and record-breaking breaches, the incredible boom of AI, novel techniques and attack chains, highly sophisticated and organized cybercrime and cyberwarfare operations, aggressive APT activity, and cybersecurity being flung into the public purview due to the cascading effects of cyber incidents that have affected hundreds of millions of people worldwide.
Negligent Oversights on Security Principles: In many breaches observed this year, there were mistakes and negligent oversights in core security concepts and practices essential for preventing cyberattacks. Organizations should be implementing strong asset and patch management; credential hardening and two-factor authentication; and the principle of least privilege in addition to managing technical debt with old or forgotten infrastructure.
Phishing Awareness Training: Phishing and the use of stolen credentials continued to be major initial access vectors this year (even for companies with otherwise strong security practices), and quality security awareness training programs need to be made a priority, with realistic phishing simulations and education on the latest phishing tactics and cyber threats performed. This is even more important with the fact that the personal data of millions of citizens worldwide has been leaked on the internet, giving adversaries troves of valuable information to use in social engineering campaigns.
Supply-Chain Risk Management: A common theme among some of the most damaging cyberattacks of the year included the preliminary compromise of a third-party partner, whose elevated access was abused to compromise the main target. Third-party/supply-chain risk management needs to be a priority for organizations.
AC: (SirPicklJohn) A full recap of this year in cybersecurity and the valuable insights it offers for 2025 and beyond can be found in this linked blog post, but the previous paragraphs represent some of the key takeaways of the year for the blue team.
[Adversary TTPs] New Developments in Attacker TTPs
In cybersecurity, there is a never-ending arms race between defenders and attackers. As the technological tools available to both sides become more advanced, this theme emerges in interesting ways! Recently-observed developments in attacker tactics, techniques, and procedures include the following:
-
LOTS (Laying Off Trusted Sites) - A similar technique to LOTL is growing in popularity, called LOTS, with trusted file-hosting sites like OneDrive, Sharepoint, and DropBox being used to host malware and add legitimacy to complex phishing campaigns.
-
WDAC EDR Bypassing - An example of MITRE ATT&CK T1562 ("Impair Defenses"), attackers with Administrator privileges can craft and deploy specifically-designed WDAC (Windows Defender Application Control) policies to block EDR sensors from loading during system boot, rendering them inoperative. This can been automated with the "Krueger" tool. The worst-case scenario would be an attacker with domain administrator privileges deploying a WDAC policy throughout an organization, systematically disabling EDR sensors on all endpoints.
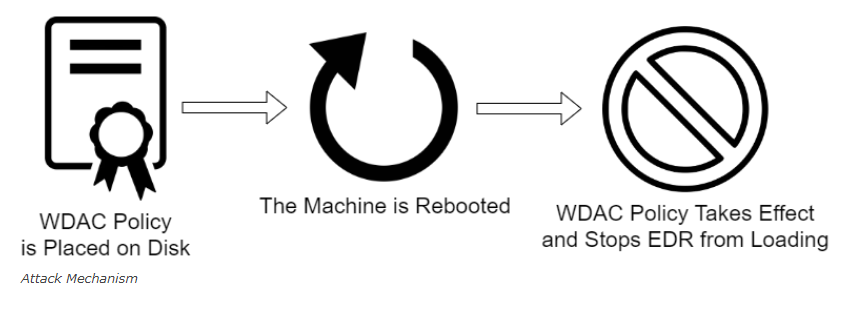
^ WDAC EDR Bypass Attack Chain ^ -
Malicious npm packages posing as Ethereum development plugins (specifically, Hardhat Runtime Environment plugins and the Nomic Foundation), targeting developers to steal private keys, mnemonics, configuration files, and more sensitive information. You can find IoC's at the bottom of this linked article.
-
Additionally, there have been major improvements in dark web/adversary KYC bypass operations (KYC stands for "Know Your Customer" - verification mechanisms for financial institutions to prevent fraud, money laundering, and terrorist financing):
- At a basic level, unsophisticated KYC-authentication mechanisms have been bypassed with static images or printed photos.
- At a mid-tier level, deepfake technologies, face-swapping software, and authentic identity documents willingly provided by victims for a short-term financial reward have been used to mimic the real-time verification process.
- Recently, more advanced attacks have used customized AI models and 3D animation to create synthetic faces that even defeat "highly-sensitive liveness detection frameworks". This shows the challenges that KYC-dependent systems like banking, crypto platforms, and other high-security industries face.
AC: (SirPicklJohn) This all goes to show that cybersecurity is a process, and not a product, and that a layered defense in depth strategy that includes more than just prevention is key in defending against modern adversaries. Also, for recent developments in social engineering TTPs used in the wild, check out the previous intelphreak report.
[Major Incident] Popular Chrome Extensions Hijacked in Major Web-Browser Supply Chain Attack, Exposing 2.6 Million Users
Happy New Year! A sophisticated campaign dating back since at least May 2024 has hijacked at least 36 Chrome extensions in the AI, VPN, general productivity, and miscellaneous spaces. Malicious versions of these extensions were released to the public with injected code that steals user session cookies and credentials. A majority of the malicious extensions were published in December 2024, and the cybersecurity company Cyberhaven was the first to disclose that their extension had been compromised in the same month. Over 2.6 million users were targeted and exposed in the campaign (around 400,000 are known to be compromised by Cyberhaven’s extension alone) and many of the web extensions have not yet been patched, still containing the malicious code. The majority of the attacker’s infrastructure went offline on December 31st, but it is still unclear whether all of the attacker’s infrastructure is offline or not.
The attack chain started with a phishing email impersonating the web store (view screenshot here) being sent to the extension developer’s publicly-available email address (provided on the web store for debugging purposes). After clicking “Go To Policy“ in the phishing email, they are redirected to a legitimate Google OAuth page (view screenshot below) with an app called “Privacy Policy Extension“ (an example of a malicious “Shadow SaaS App“) requesting edit, update, and publishing access to the themes, apps, and licenses that the developer’s Google account owns. The attacker then used this access to publish a new version of the extension with the malicious code injected.
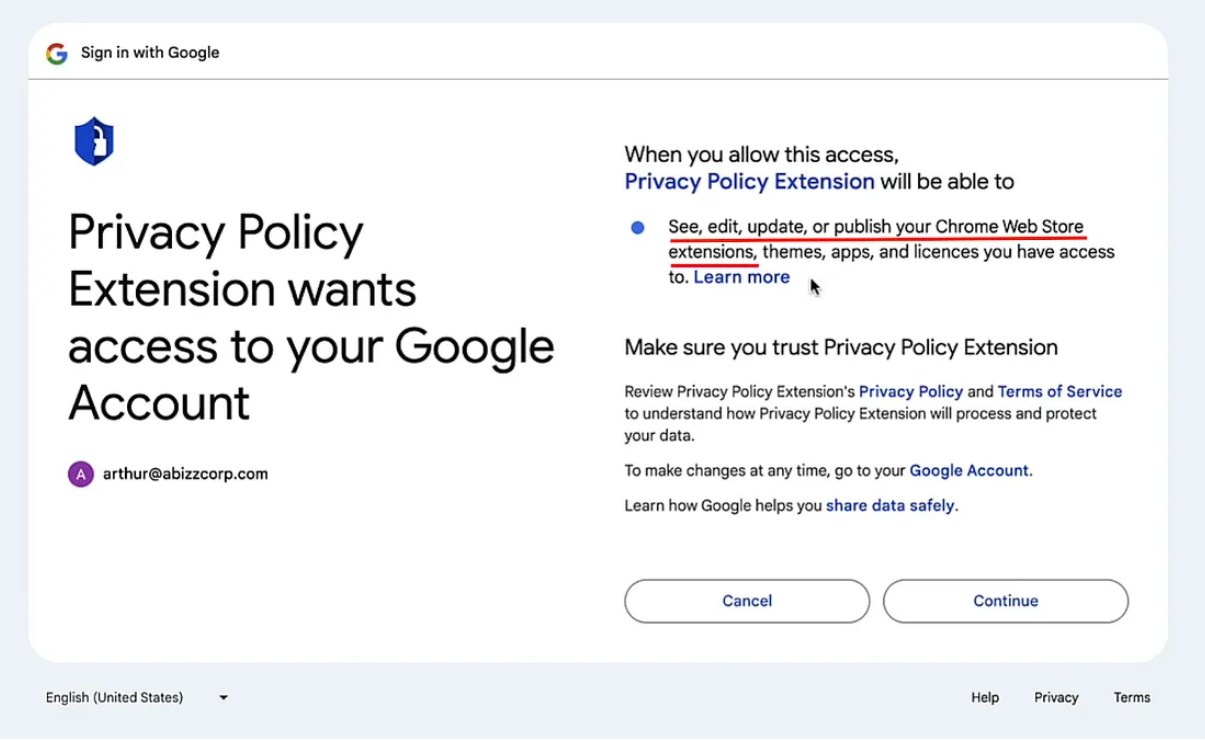
^ Malicious OAuth Consent Request from the Attacker's Shadow SaaS App ^
REMEDIATIONS AND MITIGATIONS: Affected users should…
- remove the compromised extensions or upgrade to known-safe versions;
- rotate all passwords and API tokens;
- clear browser data, sessions, and/or reset the browser to original defaults;
- review logs for malicious activity/IoCs, an extensive list of which can be found at the bottom of the live incident feed from ExtensionTotal; and
- limit their browser extensions to only those that will be used regularly.
Additionally, Browser Detection and Response (BDR) solutions exist that specialize in detecting and preventing these kinds of attacks!
AC: (SirPicklJohn) For a full rundown of the attack chain, consult SquareX’s report on the incident. For more technical information on the actual compromise of the extension and the malicious code, as well as a rundown of the incident (note that some of the information is outdated), consult SecureAnnex’s report. A running list of the compromised extensions, including extension IDs, affected versions, affected user count, and patched versions (if available) can be found in this Google Sheet.
[Major Incident] Japan Airlines Hit with a DDoS Cyberattack During Holiday Travel Season
Japan Airlines faced a DDoS-style cyberattack on Thursday, December 26th that disrupted over 20 domestic flights by less than 1 hour. Japan Post Co. confirmed that the flight delays affected postal deliveries. Within hours, the airline was able to identify the root cause and restore system functionality. The source of the problem was a flood of network traffic to their network that connects their internal & external systems. The goal was to flood the network with transmitted data, causing delayed responses or full outages.
AC: (ResidentGood) One takeaway from this event is any key information systems that connect to the outside world must have appropriate & redundant DDoS protections in place. These can include firewalls, intrusion prevention systems, and rate-limiters. Another key takeaway is the importance of establishing patterns of normal network activity & using live monitoring to identify anomalies that could signal an attack.
Other Japanese airlines did not seem to face a similar attack, and Japan Airlines claims no customer data was breached. They also said they did not find any evidence of malware infection. As Japan strengthens defense ties with western countries like the US, experts like Dennis Blair (Former US Director of National Intelligence) have cited cybersecurity shortfalls as a liability to the security alliance. In the past 2 years, Japan’s aerospace & transportation industry have faced multiple cyberattacks.
[Law] Italy Hits OpenAI with €15 Million Fine Over Data Privacy Violations
An Italian data protection watchdog, Garante, has found OpenAI to be in violation of the GDPR with ChatGPT’s user data collection practices. Garante’s investigation found that OpenAI used personal data to train ChatGPT without sufficient legal basis and transparency. OpenAI was said to have failed to disclose a breach in March of 2023. It was also found that ChatGPT did not provide an adequate way to verify a user's age. Garante has issued a fine of 15 million euros ($15.4 million USD) and OpenAI was ordered to do a 6 month communication campaign across all forms of media. The purpose of the campaign would be to educate the public on how to protect their data from being used to train generative AI models. OpenAI disagrees with the decision and is seeking an appeal. OpenAI has stated they previously worked with Garante in 2023 to make changes in order to offer ChatGPT in Italy again after its initial ban.
AC: (ResidentGood) The case is not finalized as OpenAI is working through the appeals process. This is a landmark story in the journey to regulate AI and protect user’s data. Companies that provide generative AI products must learn how to navigate compliance issues that arise from the training of their models. This is one of many cases to come where AI companies draw the ire of legislators. One way that AI companies can avoid such large consequences is to proactively educate their users about how their data is used to train AI models, and how to prevent their data being used in such manner. For more information, view Garante’s press release here.
[Law] HHS Proposes Updates to HIPAA Cybersecurity Rules
The US Department of Health & Human Services has published a public notice about proposed changes to the HIPAA Security Rule.
Some of the notable proposed changes include:
- Requiring written procedures to restore downed IT systems and lost data within a 72 hour period.
- Requiring annual system audits for compliance, as well as annual certified verification that business partners are using safeguards to protect Electronic Protected Health (ePHI) information.
- Requiring an updated inventory of technology assets and network maps, especially when ePHI is involved.
- Requiring analysis of information assets & systems to priority of restoration.
- Requiring written incidence response plans, including how personnel can report security incidents.
- Requiring documentation on how regulated entities will test and revise their incident response plans.
- Requiring encryption of ePHI both in rest and in motion.
- System hardening such as removal of extraneous software on systems that deal with ePHI and implementing anti-malware protection.
- Requiring MFA where its applicable.
- Requiring network segmentation.
AC: (ResidentGood) People, companies, and organizations are welcome to submit comments on the proposal here by March 7, 2025. These proposed changes would be an improvement of healthcare cybersecurity regulation. However if these changes do take place, organizations that are regulated under HIPAA must be prepared to adjust their operations accordingly. Some companies state that these changes could require regulated entities to make significant investment in their infrastructures to remain compliant. This could be a challenge for certain organizations, especially the smaller ones.
[National Security] Lazarus Group Targets Nuclear Industry
Researchers from Kaspersky reported that the North Korean APT "Lazarus Group” is carrying out a new malware campaign. This malware has targeted at least 2 employees that work in the nuclear industry. The attack comprises of a downloader, a loader, and a modular backdoor. It begins with VNC (remote access software) trojans that impersonate a skills test for a lucrative job opportunity and trick the user into interacting with it. ISO & ZIP files were used to make detection harder. Most of the C2 servers used by the various malwares are compromised WordPress servers. The infection chain is quite complex, using the initial VNC trojans to install other loaders that in turn load backdoors, RATs (RollMid) & infostealer-dropper combos (LPE Client). See the image below for a better idea of one of the observed attack chains:
Researchers believe these attacks are part of a larger cyber espionage campaign that is being tracked under the names “Operation Dream Job” & “NukeSped”. The campaign is based around conducting espionage by targeting developers and other professionals with unsolicited but attractively lucrative job opportunities. These skills tests and job postings are a mask for software that deploys and downloads malware onto the user’s system. Industries targeted include Defense, Aerospace, and even cryptocurrency. North Korean APTs have been gradually becoming more effective in funding their operations with successful attacks on crypto organizations around the globe.
AC: (ResidentGood) The Lazarus Group has historically only used a few modular malware frameworks. CookiePlus proves that they are pivoting to new modular malware techniques and are constantly improving their tactics. Researchers say this malware appears to still be under development, so further advancement is expected. Part of what makes detecting CookiePlus difficult is that it acts like a normal downloader, making it hard to distinguish malicious payloads from real ones. Having staff that is well & regularly trained against the newest social engineering & phishing attacks can help mitigate attacks like this.
[National Security] Chinese Nation-State Actors Breach US Treasury via Cybersecurity Vendor
The US Department of the Treasury had a data leak through a cybersecurity vendor, BeyondTrust. According to the Treasury’s letter to lawmakers, no classified information was reported to have been stolen. The attacker is suspected to be a Chinese APT. This is why the Treasury has stated that this is being treated as a “major incident”. Hackers were able to gain access to an API key used to provide cloud tech support to Treasury users. How exactly they attained this key is unknown right now. Stealing this key allowed the APT to access Treasury systems and exfiltrate information. Once BeyondTrust had knowledge of the incident, they removed the API key that was breached and notified the Treasury. The threat actors have no known persistence in Treasury systems, and the BeyondTrust service was taken offline. In addition to the Treasury, the Intelligence Community, FBI, CISA, and third-party forensics investigators are continuing to examine the incident.
AC: (ResidentGood) This is one of many cyber espionage attacks that the Chinese have been carrying out as geopolitical tensions rise between China & the United States. Cybersecurity vendors, especially those that service public sector clients, should operate carefully because they have a large target on their back. Organizations who depend on third-party technical partners must ensure these parties are putting appropriate security measures in place and responding to incidents effectively. As normally observed with these types of incidents, the Chinese government has yet to comment. Diplomacy becomes difficult in these situations with a lack of transparency & accountability between nations.
END REPORT
If you are interested in anything Cybersecurity, come check out our Discord!
Sources:
2024 Cybersecurity Recap and Insights for the Future:
- National Public Data breach: What you need to know. (n.d.)
- Blackfog - Managing Expectations and Job Satisfaction For IT Security Leaders (October 9, 2024)
- What 2024’s Worst Cyberattacks Say About Security in 2025 (December 27, 2024)
- The biggest cyber attacks of 2024 (September 5, 2024)
- File hosting services misused for identity phishing (October 8, 2024)
- Ukraine: Hack wiped 2 petabytes of data from Russian research center (January 26, 2024)
- GUR specialists conduct successful cyberattack on company implementing information systems into Russian industry (January 27, 2024)
- Moobot Malware FBI Affadavit and Search and Seizure Warrant (January 26, 2024)
- Year in Review: The Most Significant Cyberattacks of 2024 (December 2, 2024)
- Data Breaches That Have Happened in 2022, 2023, 2024, and 2025 So Far (January 2, 2025)
- Top Data Breaches in 2024 [Month-wise] (September 10, 2024)
- Cybersecurity News Round-Up 2024: 10 Biggest Stories That Dominated the Year (December 10, 2024)
- 2024 in review: Hacks, hacks and more hacks (December 27, 2024)
- 10 of the biggest cybersecurity stories of 2024 (December 23, 2024)
- What 2024’s Worst Cyberattacks Say About Security in 2025 (December 27, 2024)
- Microsoft Digital Defense Report 2024 (October 25, 2024)
- Stop saying “technical debt” - StackOverflow (December 27, 2023)
- Ransomware and Cyber Extortion in Q2 2024 (July 15, 2024)
New, Non-SE Attacker TTPs:
- Security pros overestimate MFA: 6 techniques hackers are using to bypass it. (December 31, 2024)
- File hosting services misused for identity phishing (October 8, 2024)
- Researchers Uncovered Dark Web Operation Acquiring KYC Details (December 26, 2024)
- New Sophisticated Attack Weaponizes Windows Defender to Bypass EDR (December 25, 2024)
- Malicious npm Packages Attacking Developers To Steal Sensitive Data Including Private Keys (January 3, 2025)
- Using WDAC to Disable EDR - Krueger (December 30, 2024)
Chrome Extension Hijacking - Web Browser Supply Chain Attack:
- SquareX Researchers Uncover OAuth Vulnerability in Chrome Extensions Days Before Major Breach (December 30, 2024)
- Cybersecurity firm's Chrome extension hijacked to steal users' data (December 27, 2024)
- Hackers Hijacked 16 Chrome Extensions to Inject Malicious Code (December 30, 2024)
- Cyberhaven’s OAuth Identity Attack — Are your Extensions Affected? (December 31, 2024)
- Cyberhaven Extension Compromise (December 26, 2024)
- Cyberhaven Incident - Ongoing Updates (Last update on January 1st, 2025)
- Breaking: Cyberhaven Chrome Extension Compromised in Holiday Attack Campaign (December 26, 2024)
Japan Airlines hit by a cyberattack, delaying flights during the year-end holiday season:
- Airline hit by a cyberattack, delaying flights during the year-end holiday season (December 26, 2024)
- Japan Airlines Was Hit by a Cyberattack, Delaying Flights During the Year-End Holiday Season (December 26, 2024)
- A cyber attack hit Japan Airlines delaying ticket sales for flights (December 26, 2024)
Italy SLAMS OpenAI with €15 Million Fine Over Data Privacy Violations:
- Italy’s privacy watchdog fines OpenAI for ChatGPT’s violations in collecting users personal data (December 20, 2024)
- Italy Fines OpenAI €15 Million for ChatGPT GDPR Data Privacy Violations (December 23, 2024)
Proposed Updates to HIPAA Security Rule Mandate:
- Proposed updates to HIPAA Security Rule mandate to restore the loss of certain relevant electronic information systems and data within 72 hours (January 1, 2025)
- New HIPAA Rules Mandate 72-Hour Data Restoration and Annual Compliance Audits (December 30, 2024)
- HIPAA Security Rule Notice of Proposed Rulemaking to Strengthen Cybersecurity for Electronic Protected Health Information (December 27, 2024)
Lazarus Group Spotted Targeting Nuclear Engineers with CookiePlus Malware
- Lazarus Group Spotted Targeting Nuclear Engineers with CookiePlus Malware (December 20, 2024)
- Lazarus APT targeted employees at an unnamed nuclear-related organization (December 23, 2024)
Chinese Hackers Breach US Treasury
- Chinese State Hackers Breach US Treasury Department (December 30, 2024)
- US Treasury Department outs the blast radius of BeyondTrust's key leak (December 31, 2024)




