Intelphreak - 12:30Z June 25th, 2024
EU Delays Vote on Surveillance Legislation, CDK Global Cyber Attacks, Espionage Actor Persists via Fortinet/Ivanti/VMWare CVEs, AI & Hydrogen Firms Partner with Nuclear Energy Companies, Army Debuts New AI Program, SneakyChef Deploys SugarGh0st Malware, US Government Clamps Down on Kaspersky

Precedence: Routine
BLUF: EU Chooses to Delay Vote on Invasive Surveillance Legislation, SaaS Provider CDK Global was Hit with Multiple Cyber Attacks that Disrupted Thousands of Dealerships, Chinese Espionage Actor UNC3886 Persists via Fortinet/Ivanti/VMWare CVEs, AI & Hydrogen Firms Partner with Nuclear Energy Companies, Army Debuts New Generative AI Program, Chinese APT SneakyChef Deploys SugarGh0st Malware, US Government Clamps Down on Kaspersky Labs & Their Distributors
BEGIN TEARLINE
[Law] EU Delays Vote on Chat Controls via Message Scanning:
The EU Council has delayed a vote on the controversial measures to scan all messages, including those on encrypted chat platforms for CSAM1. The measure was proposed by Belgium, the current president of the EU. This is another version of the proposal from the EU Commission in 2022 for client-side
scanning of all chat messages. Experts in the industry have said this legislation would severely violate the privacy rights of citizens and is prone to generating many false positive for suspicious material. Many platforms threatened to leave the EU base if this was passed. Notably, the president of the Signal Foundation, Meredith Whittaker, said this proposal fundamentally undermines encryption2.
AC: : It is certainly a priority to keep platforms safe from abusive material such as CSAM. This delay does not mean total abandonment of such a policy. It is likely the policy will be revised and eventually proposed to vote on again. The violation of end-to-end encryption does not only affect criminals. Many innocent citizens use E2EE to secure their communications from nefarious actors in a world where data breaches are common.
[Cybercrime] CDK Global Cyberattacks:
CDK Global, a SaaS company that services many car dealerships across the nation was his with two cyberattacks this past week. The service is a central platform for managing the operations & data of car dealerships. The first attack required CDK to take 2 data centers offline which disrupted services3. The next day as CDK attempted to restore some systems, they were hit with another attack which made them further disrupt services4. These attacks not only disrupt the operations of car dealerships but also consumer ability to purchase cars.
AC: These attacks are severely disruptive, and the timing is interesting. Rumors say that CDK suffered a ransomware attack and disrupted services to prevent its spread. These events can teach a valuable lesson. While SaaS platforms over many benefits, and the liability is deferred to a third party in these events, breaches of these platforms are still possible. While the client may not be subject to all of the liability, they still must face the consequences of business disruption. This must be carefully considered when aiming to implement a central operations platform. Continuing operations in the event of service loss is vital to a clients operations planning.
[Cybercrime] China-Based Espionage APT UNC3886:
UNC3886, the Chinese linked espionage actor has been observed maintaining persistence on systems they have compromised using their zero-days of Fortinet, Ivanti, and VMWare5. The targets are entities in North America, Southeast Asia, Oceania, Europe, Africa, and other parts of Asia. They have targeted several sectors including: Government, Telecoms, Tech, Aerospace, Military, and Energy/Utility. They used public rootkits on guest VMs using SEAELF as an installer6. They also delivered backdoors that utilize services like Github & Google Drive for Command-and-Control servers.
AC: The CVEs used in these persistences are not new, and therefore if your organizations have followed the advisories, you should be safe from persistence. Affected organizations should follow the Fortinet and VMware advisories to harden against further threats. Anytime an organization uses a service, they should keep an eye for advisories and vulnerabilities in order to stay safe from threats like these. A failure to remedy any disclosed vulnerabilities can lead to even further damage like information extraction.
[New Tech] AI Firms Cut Deals with Nuclear Energy Firms:
AI Firms & Hydrogen producers are partnering with the nuclear industry to meet energy demands7. These firms are collocating their data centers with nuclear plants to get power before the meter. They are also using carbon-free energy exchanges to buy nuclear energy on demand to meet computing needs. Many questions and concerns have been raised surrounding this trend.
AC: Deals like these can have huge impacts in a society where Large Language Models, Crypto Mining, and Quantum Computing are becoming more common. A lot of technological innovation never makes it to market due to energy concerns. While nuclear energy has safety & environmental concerns, it also seems to be the best candidate for meeting immense computing demands.
[New Tech] Army Teases Generative AI Program:
The US Army’s Acquisition, Logistics & Technology division is exploring the production of a generative AI program length, menial tasks like contract drafting8. It will operate at the highest level possible of handling unclassified information, Impact Level 5. The LLM will be exclusively trained on the Army’s data.
AC: This is an interesting use of modern LLM technology. The government contracting process is one that full of tedious paperwork, and repetitive tasks. Algorithms like this could eventually speed up this process and improve the productivity of the federal contracting sector. Applied to defense this could mean getting state of the art technology on the field at a faster rate.
[National Security] China-Linked APT SneakyChef Deploys Espionage Software:
Talos intelligence has unearthed a threat group names SneakyChef who are operating a malware named SugarGh0st9. The group uses scanned government documents to bait targets. Due to the language used, this group is thought to be Chinese in origin
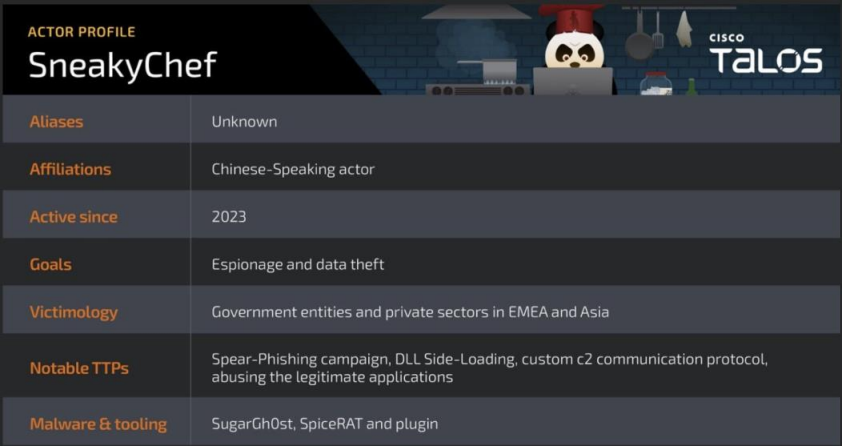
Targets include government ministries in Angola, Latvia, Kazakhstan, Turkmenistan, India, and Saudia Arabia. SugarGh0st is the next phase of evolution in the Gh0st RAT framework10. Once loaded on the
machine, the malware collects tons of system information such as hostname and file structure.
AC: This threat group is very sophisticated. These lures ultimately amount to sophisticated social engineering. The group used copies of publicly available documents from each ministry and edited the files to make it appear as legitimately important while concealing a vicious payload. Organizations, especially government ministries, should proceed by training their key staff on anti-social engineering. Teaching leadership who has access to high-value assets to avoid bait like these, and to report it to the security team is the best course of action.
[National Security] US Government Bans Kaspersky Software:
On June 20th, the Department of Commerce placed a ban on Kaspersky Lab Inc (and its affiliates) from providing their services to the United States, citing concerns of national security11. These national security issues stem from Kaspersky’s collaboration with the Russian Government. Kaspersky has denied these allegations as they always have. Customers will be unable to buy any new software products from Kaspersky beginning around July 24 of this year12. Some background on this issue is that Russia has expanded surveillance laws regarding online communications and internet traffic, placing stricter controls over what they can see13. Several official distributors of Kaspersky software have said
this ban is annoying, burdensome, and is forcing them to make tough business decisions in order to stay afloat14.
AC: Considering the current state of geopolitical tensions, this move is not surprising. There has yet to be substantial evidence provided of these claims. Any company operating in a nation is subject to the regulations of that nation. Perhaps the concern is the potential for the Russian Government to influence Kaspersky to add malicious code to their software products. Current users have about 100 days to download Kaspersky, resell it, and get updates.
END TEARLINE
Final Analyst Comments:
Many events that have occurred have a severe impact on the state of national
security. Legislative clamp downs on foreign software vendors. A stagnated attempt to implement a wide net policy of surveilling chat applications with no regard for encryption. A potential solution to the snowballing demand for computing energy. Encryption is a fundamental to ensuring privacy and data security. The EU’s attempt to override this, while understandable, is not quite the solution society needs to combat CSAM. With rising political tensions and global conflicts, keeping a close eye on what states influence what large companies can help our nations stay ahead of the curve. We must not fight advanced technology but leverage interdisciplinary innovations to solve emerging problems.
Analyst: ResidentGood
END REPORT
If you are interested in anything Cybersecurity, come check out our discord
Sources:
- https://stackdiary.com/eu-council-has-withdrawn-the-vote-on-chat-control/
- https://thehackernews.com/2024/06/signal-foundation-warns-against-eus.html
- https://www.bleepingcomputer.com/news/security/cdk-global-cyberattack-impactsthousands-of-us-car-dealerships/
- https://www.bleepingcomputer.com/news/security/cdk-global-hacked-again-whilerecovering-from-first-cyberattack/
- https://thehackernews.com/2024/06/chinese-cyber-espionage-group-exploits.html
- https://www.csoonline.com/article/2156359/fortinet-ivanti-zero-day-victims-face-evolvedpersistence-by-the-espionage-actor.html
- https://www.energyintel.com/00000190-3035-d824-a7d5-733fa0950000
- https://breakingdefense.com/2024/06/army-teases-pilot-generative-ai-program-to-start-injuly/
- https://blog.talosintelligence.com/sneakychef-sugarghost-rat/
- https://interestingengineering.com/science/sugargh0st-sneakychef-cyberespionage
- https://home.treasury.gov/news/press-releases/jy2420
- https://techcrunch.com/2024/06/26/how-the-kaspersky-ban-will-hit-resellers-in-the-us/
- https://www.axios.com/2024/06/25/kaspersky-ban-russia-geopolitical-history
- https://arstechnica.com/tech-policy/2024/06/citing-national-security-us-will-ban-kasperskyanti-virus-software-in-july/



