Intelphreak - 4:00Z July 15th, 2024
Increased Hacktivisim Until 2025, NSA Release on PRC APT, AllHere Faces Financial & Privacy Trouble, Shopify Data Breach Origin, Ticketmaster Leaks, RADIUS Vulnerability, Espionage Groups Using ORB Networks, OpenSSH Vulnerability Allows RCE, Research Says Attackers Exploited a Windows Zero-Day

Precedence: Priority
BLUF: Increased Risk of Hacktivisim Until February 2025, NSA Releases Case Studies on Threat Group Sponsored by PRC, AI Firm AllHere Faces Financial Troubles & Claims of Violating Privacy Policies, The Shopify Data Breach Originated from a Third Party Application, Ticketmaster Tickets Have Been Leaked for Multiple Events, Auth-As-Anyone Vulnerability was Discovered in RADIUS, Chinese Cyber-Espionage Groups Are Using Complex ORB Networks to Attack, New OpenSSH Vulnerability Presents Risk of Remote Code Execution, Researchers Say Attackers Exploited a Zero-Day For a Year to Deploy Malware to Windows Systems via Internet Explorer
BEGIN TEARLINE
[National Security] NSA Releases Case Studies on China-Sponsored Threat Group:
The National Security Agency & the Australian Signals Directorate have collaborated on a case study of a PRC-sponsored threat actor that is known to the industry as “APT 40”, “Kryptonite Panda”, “GINGHAM TYPHOON”, and “Bronze Mohawk.”12 The group has targeted government organizations in the United States and Australia. The group continually performs reconnaissance on organizations’ networks to look for and exploit vulnerabilities with a quick turnaround time.
AC: : APT40 has exploited vulnerabilities in popular software such as Log4J, Atlassian Confluence, and Microsoft Exchange. Some techniques defenders can employ to protect themselves include implementing comprehensive logging over time, patching all publicly exposed devices, segmenting networks to minimize lateral movement, closely monitoring services to ensure their hardening, and disabling unnecessary network services, ports, and protocols. View the full report for more information.
[New Tech] Whistleblower Claims AllHere Mishandled Data of LAUSD Students:
AllHere, the company behind the school chatbot “Ed” recently faced financial issues and furloughed many of its employees1. A former employee levied allegations against the company for mishandling student data. They claim AllHere sent student data to multiple partner companies against the policies of the LA Unified School District. AllHere signed a $6.2 million contract with LAUSD, $3 million of which was paid before the company had financial troubles2. AllHere worked as a consultant and LAUSD retained ownership of the AI chat technology. Therefore, they were subject to following the LAUSD privacy policies. Prompts contained students’ personal data even if unrelated, and these prompts were shared with third parties.
AC: This story serves as an important development in the use of AI in the education sector. Education systems must practice strict data handling practices as academic records can contain lots of Personally Identifying Information (PII). LAUSD has good reason to investigate for any breaches resulting from this ordeal. They have faced two instances of data breaches in the past few years. For example, in 2022 a threat actor named “Satanic Cloud” claimed ownership of 24 million student records from the LAUSD3.
[Cybercrime] Shopify Data Breach Did Not Originate from Its Systems:
On July 3rd, a Breach Forums user going by the monicker “888” published a post for selling Shopify data including names, emails and phone numbers4. Shopify has confirmed that this breach happened and did not come from its infrastructure. The company did not mention the name of the app and how many users were affected. However, they said the app developer intends to notify affected users.
AC: The breach contains a plethora of PII so anyone who was compromised faces risk of phishing and other social engineering methods. Since they did not disclose the name of the application, all organizations with Shopify in their stack should keep an eye out for notification of breach. The prescribed remedy is to monitor your Shopify account for unusual activity, change passwords maintaining a high degree of strength, ensure Multi-Factor Authentication is enabled, and keep an eye out for strange communications requesting personal info.
[Cybercrime] ShinyHunters Leak Ticketmaster Tickets for Multiple Artists/Events:
The threat actor ShinyHunters has been extorting Ticketmaster under the alias “Sp1derHunters”6. They have been threatening to release tickets to several major events and have made good on those promises by releasing almost 40,000 tickets. Events whose tickets were leaked include Taylor Swift, Pearl Jam, Foo Fighters, and Phish. Ticketmaster has responded by denying claims it offered the group $1 million for the data, and that it has ticket protection technology that changes ticket barcodes every few seconds to protect them from unauthorized use.
AC: This is a massive breach from a major company that controls ticketing for most artists & events in the US. The breach allegedly originates from ShinyHunters compromising the Snowflake cloud of Ticketmaster5. The threat actor has compromised the Snowflake databases of at least 165 organizations. If your organization uses a Snowflake cloud, it is advised to investigate potential breaches of sensitive data. Ensure your organization is protected from any vulnerabilities that have been identified surrounding Snowflake’s technology.
[Research] RADIUS Vulnerability CVE-2024-3596:
Cloudflare and other security researchers have discovered a critical vulnerability in RADIUS that allows a Man-in-the-Middle attacker to forge an accept response even when the user was not authenticated successfully8. The main security of RADIUS derives from an MD5 hash algorithm deemed cryptographically broken as of 2008 due to collision attacks10. You are vulnerable if you use PAP, CHAP, MS-CHAPv2, and other non-EAP protocols over UDP9.
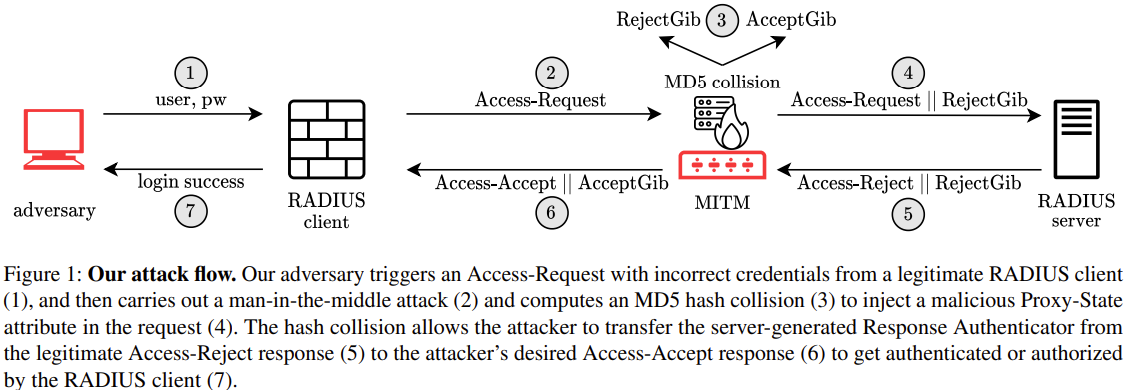
AC: This is a fundamental vulnerability to RADIUS and systems administrators who use RADIUS should check with vendors for any security patches7. Move to RADIUS/TLS or tunnel RADIUS traffic. Both RADIUS clients and servers should be patched. For more information view the whitepaper.
[Research] Chinese Cyber-Espionage Groups Using ORB Networks Mandiant Warns:
Chinese Cyber groups have evolved in their approach to cyber-espionage. Analysts from Mandiant have recently spoken about the use of a complex IaaS Operational Relay Box network11. This network comprises of a vast array of Virtual Private Servers, compromised routers, and compromised smart devices (IoT). This network has five layers: Chinese servers managing nodes, Chinese/Hong Kong based VPSs where attackers authenticate and deliver traffic, traversal nodes which are the majority of nodes, exit nodes that connect the ORB network to the victim, and finally the victim’s server.
AC: This type of network makes blocking attacker IPs via firewall almost impossible due to the number of different IPs that attackers can use. Mandiant suggests rather than using IP Addresses as Indicators of Compromise, look for these ORB networks using behavior-based signatures. Look for patterns in attacker infrastructure such as what types of devices are they compromising.
[Research] CVE-2024-6409 Allows Possible Remote Code Execution via OpenSSH:
Security researcher Solar Designer has discovered a bug in OpenSSH that allows the possibility of Remote Code Execution due to a race condition in signal handling during the privsep child process13. This is where it is distinct from CVE-2024-6387 that affects the parent processes with higher privileges. This makes it not as high a priority as CVE-2024-6387. However, users of Red Hat Enterprise Linux 9 should be sure their version is not affected by the CVE.
AC: This vulnerability particularly affects version 8.7p1 and 8.8p1 of OpenSSH that were shipped with Red Hat Enterprise Linux 9. It is advised to install the latest security patches for your ssh servers and any other that could be impacted. You should also limit SSH access through network controls & enforce network segmentation.
[Research] Researchers Discover Zero-Day That Hackers Use to Deploy Malware to Windows Users:
Attackers used a zero-day exploit in Windows for a year before Microsoft was able to patch it on Tuesday, July 9th. The exploit appends the “.url” extension to what appears to be a regular PDF file, tricking the user into clicking it14. A link in the file makes a special call that opens Internet Explorer. With the file open in Internet Explorer, attackers could exploit IE’s outdated codebase to deploy malware onto the Windows system.
AC: After all this time, Internet Explorer still proves to be a source of hassles. This exploit affects both Windows 10 & Windows 11 hosts. The firm Check Point who pointed out the flaw has released six hashes for malicious files that users can check against their file systems to see if they have been affected.
END TEARLINE
Final Analyst Comments:
With the US election this year, we have seen incidents of cyber-attacks on infrastructure & politically motivated hacks16, 17. Leading up to the presidential election (and for a few months after) there is an increased risk of cybercrime & cyber-espionage operations targeting US organizations/agencies. Particularly be wary of social engineering campaigns, data breaches, and ransomware attacks as those have been the most common ones this year. It is advised to harden your systems, particularly legacy/EOL systems. Update and stay consistent with anti-phishing training. Stay up to date with any disclosed vulnerabilities affecting your tech stacks. Ensure you have solid DDoS protection.
Analyst: ResidentGood
END REPORT
If you are interested in anything Cybersecurity, come check out our discord
Sources:
- https://www.the74million.org/article/whistleblower-l-a-schools-chatbot-misused-studentdata-as-tech-co-crumbled/
- https://pivot-to-ai.com/2024/07/10/la-school-chatbot-vendor-goes-bust-student-data-at-risk/
- https://www.the74million.org/article/l-a-schools-investigates-data-breach-as-fcc-approves200m-cybersecurity-pilot/
- https://cyberinsider.com/shopify-data-breach-impacting-180000-users-tied-to-third-partyapp/
- https://www.bleepingcomputer.com/news/security/hackers-leak-alleged-taylor-swift-ticketsamp-up-ticketmaster-extortion/
- https://www.bleepingcomputer.com/news/security/hackers-leak-39-000-print-at-hometicketmaster-tickets-for-154-events/
- https://infosec.exchange/@tychotithonus/112756492570080182
- https://www.blastradius.fail/
- https://thehackernews.com/2024/07/radius-protocol-vulnerability-exposes.html
- https://arstechnica.com/security/2024/07/new-blast-radius-attack-breaks-30-year-oldprotocol-used-in-networks-everywhere/
- https://www.darkreading.com/cybersecurity-operations/chinese-orb-networks-conceal-aptsmake-tracking-iocs-irrelevant
- https://www.nsa.gov/Press-Room/Press-Releases-Statements/Press-ReleaseView/Article/3830375/nsa-joins-in-releasing-case-studies-showing-prc-tradecraft-in-action/
- https://thehackernews.com/2024/07/new-openssh-vulnerability-discovered.html
- https://arstechnica.com/security/2024/07/threat-actors-exploited-windows-0-day-for-morethan-a-year-before-microsoft-fixed-it/
- https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2024-38112
- https://www.wsj.com/politics/national-security/fbi-director-says-china-cyberattacks-on-u-sinfrastructure-now-at-unprecedented-scale-c8de5983
- https://www.techrepublic.com/article/pro-russia-hacktivists-target-operational-technology/



