Intelphreak - 10:30Z July 22nd, 2024
CrowdStrike Outage, Delinea Fixes Privilege Vulnerability, Malicious NPM Packages Discovered, Cisco Patches Secure Email Gateway, Rite Aid Data Breach, Ransomware Group Continues ESXi Exploitation, FIN7 Rebrands to Sell Malicious Tools, New Research on APT41, Treasury Sanctions Russian Hacktivists

Precedence: Routine
BLUF: CrowdStrike Update Triggers Global IT Chaos & Fixes Are Released, Delinea Releases Fix for Privilege Escalation Vulnerability Discovered by CyberArk, Two Malicious NPM Packages Mimic AWS Multipart Copy to Load Backdoors on Hosts, Cisco Patches Vulnerability in Secure Email Gateway That Allowed Unauthenticated Users to Modify Host Files, Rite Aid Notifies 2.2 Million Customers of Data Breach Including PII, Ransomware Group SEXi Changes Names & Continues to Exploit VMware ESXi Servers, FIN7 Rebrands to Sell EDR Bypass Tools & Automates SQL Injection Attacks, Mandiant & Google’s TAG Publish New Research on APT41, US Treasury Sanctions Key Members of Russian Hacktivist Group Cyber Army of Russia Reborn
BEGIN TEARLINE
[Major Incident] CrowdStrike Update Crashes IT Systems Around the Globe:
CrowdStrike pushed a faulty update to Falcon that caused Windows hosts to crash around the world2. CrowdStrike was able to identify the issue and issue a patch for its Falcon Sensor software. Users can install the latest updates via the Support Portal to get the fixed version1. The BSODs were caused by the driver update not being formatted properly, causing Windows to crash. The company’s shares felt a sharp market correction as clients across nearly every sector faced disruption to their operations. Threat actors have been capitalizing on the incident via phishing campaigns, disguising malicious code as a CrowdStrike patch3.
AC: : : It was a great weekend for memes as this event became one of the most widely discussed cyber incidents of this year. This fiasco had major impacts to business operations across a plethora of companies as CrowdStrike is an industry leading EDR provider. Most major airlines had to ground flights. Notably, Southwest Airlines avoided major grounding because their IT infrastructure is largely outdated, running Windows 3.1 on many hosts. This software is three decades old. Restaurants couldn’t process payments as CrowdStrike is deployed on POS systems. Hospitals had their systems crash causing logistical nightmares. Media outlets got caught up in the chaos making errors like confusing the Microsoft outage that happened recently as the cause of the CrowdStrike outage. Events like this can be avoided in future via a systemic solution involving action of both clients and vendors.
[Research] CyberArk Discovers Privilege Escalation Vulnerability in Delinea Privilege Manager:
The red team at CyberArk caught an Escalation of Privilege Vulnerability in certain versions of Delinea Privilege Manager for Windows4. They were able to exploit this to run code as System despite being an unprivileged user. The team responsibly disclosed said vulnerability along with Proof of Concept. This vulnerability has been deemed CVE-2024-39708.
AC: After disclosure, Delinea tested and released a fixed version of Delinea 12.0.1096 on July 1st. If your organization uses Delinea 12.0.1096 it is recommended to ensure you have the most updated version that contains the fix.
[Research] Researchers Discovered Two Malicious NPM Packages Containing Backdoors:
Researchers at Phylum have found two NPM packages relating AWS to be malicious, containing backdoors to compromise developer systems5. These packages have been downloaded hundreds of times. The packages in question are “img-aws-s3-object-multipart-copy” & “legacyaws-s3-objectmultipart-copy” that are imitating the legitimate package aws-s3-object-multipart-copy. The malicious packages contain the normal package code along with a file called “loadformat.js” that processes three images, one of which contains fragmented code for a backdoor.
AC: The researchers go on to discuss how this, along with other incidents of malicious code inserted in open source software, mark a growing trend in the sophistication of attacks targeting open source repositories. This vulnerability was made possible due the insufficient ability for systems to catch these malicious packages before developers can install them.
[Research] Cisco CVE-2024-20401 Affecting Cisco Secure Email Gateway:
Cisco has released a public statement about a vulnerability in their Secure Email Gateway software that allows for unauthenticated remote writes to host files.6 Improper handling of email attachments when scanning & analysis is turned on allows attackers to replace files on the user’s local system. Affected systems must be running a vulnerable version of Cisco AsyncOS, File Analysis or Content Filtering is turned on for incoming mail, and the Content Scanner Tools version is earlier than 23.3.0.4823. Cisco has released a regular update that fixes these vulnerabilities.
AC: It is great that Cisco was able to fix this vulnerability as it poses severe risks to systems running their secure email gateway. Customers with service contracts and licensed software can download the update through the usual channels. If you have purchased through a third party vendor or do not have a service contract, it is recommended to contact the Cisco Technical Assistance Center.
[Cybercrime] Rite Aid Discloses 2.2 Million Customers Had Their Data Breached:
Rite Aid had a security incident in June that compromised information of 2.2 million customers.7 In a data breach notification to Maine’s Attorney General, Rite Aid said it would start notifying affected customers. The breach compromised data on retail purchases (and attempted ones) however the products were not specified8. A ransomware group going by the name RansomHub has taken credit for the attack.
AC: Affected data mainly deals with purchases made between June 6, 2017, and July 30, 2018. After the global law enforcement operation that took down much of Lockbit’s infrastructure, RansomHub has been gaining infamy in the ransomware scene. RansomHub claims to have been in talks with Rite Aid before communications abruptly halted. Rite Aid has not confirmed this claim. If you were a Rite Aid customer in 2017 or 2018 it is best to keep an eye out for notification as personally identifiable information is a part of the breached data.
[Cybercrime] SEXi Ransomware Group Rebrands to APT Inc:
The group SEXi known for their ransomware operations has rebranded and launched more attacks9. The group appeared on the scene in February of this year for targeting VMware ESXi servers with ransomware. They attack multiple organizations across a few incidents this year. Their original name derived from the name of their ransom note files. In June they changed names to APT Inc and continued to deploy Lockbit 3 & Babuk encryptors to VMware ESXi servers.
AC: These encryptors they use are very secure and there is no known way to decrypt the data without following the ransom. Their ransom demands vary between thousands and millions of dollars.
[Cybercrime] Cybercrime Group FIN7 Using Automated Injection Attacks & EDR Bypass Solutions:
The gang of cybercriminals known as FIN7 has been using aliases to mask their identity including: “goodsoft”, “lefroggy”, “killerAV” and “Stupor.”10 They have been using these aliases to sell software that bypasses endpoint security named AvNeutralizer. AvNeutralizer has been documented for a while with previous iterations having files that mimic popular security solutions. The unpacked tool has 10 various attack techniques. Sentinel One has identified a new version of this software that exploits builtin Windows driver functionality to cause errors in protected processes, resulting in loss of service availability. Sentinel One has also linked recent attacks on public servers to FIN7 & their Auto-SQLi module that automates SQL Injection attacks. These injection attacks mostly affected companies in the manufacturing and government/public sector in 2022.
AC: Sentinel One’s research highlight the difficulty with staying ahead of cybercrime networks & their evolving techniques. The sale of such advanced attack tools means a severe increase in the risk of being attacked with them. This is a reminder that system hardening is a continuous process that must be revisited as malicious tools get more advanced. Please view the article for a comprehensive list of Indicators of Compromise.
[Cybercrime] Mandiant, Google Threat Analysis Group Observe APT41 Campaign:
Mandiant & Google’s Threat Analysis Group have worked together to document a sustained campaign by APT4111. The sectors being targeted include shipping & logistics, media & entertainment, tech, and automotive. The actor intruded networks and deployed web shells to maintain persistence (ANTSWORD and BLUEBEAM). They used these shells to download the program DUSTPAN that loads a backdoor. As they persisted, they escalated to using the dropper program DUSTRAP to decrypt malicious code that setup a communication channel. It was designed to conceal presence, exfiltrate data, and setup command-and-control structures.
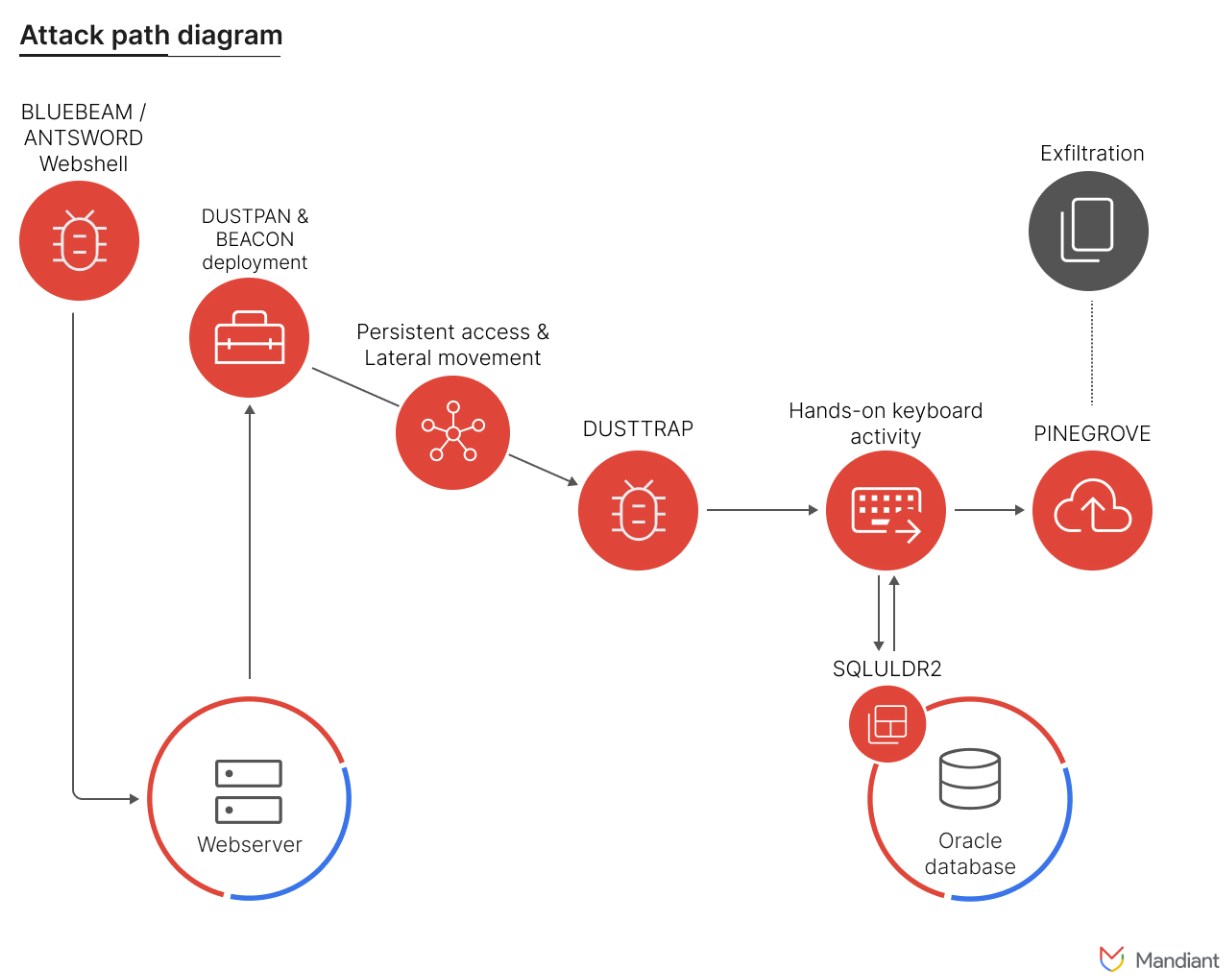
AC: APT41 has carried out espionage activity sponsored by China in the past. They also have been involved in operations that appear to be outside of China’s control. View the article for a list of Indicators of Compromise.
[National Security] US Treasury Sanctions Members of Russian-Aligned Hacktivist Group:
The US Department of the Treasury designated & sanctioned Yuliya Vladimirovna Pankratova and Denis Olegovich Degtyarenko for their roles in attacking critical US infrastructure12. The two hackers were connected to the hacktivist group Cyber Army of Russia Reborn. Last year, the group claimed attacks on the Industrial Control Systems of several U.S. and European entities. The group used simple techniques to control the industrial equipment of facilities responsible for critical water supply, hydroelectric energy, waste management, and other infrastructure.
AC: Pankratova is the face of CARR and the leader. Degtyarenko is one of the primary hackers for the group. Therefore, these sanctions make sense as they are responsible for major threats to western infrastructure. The surprisingly unsophisticated attacks of this group gave them control of major equipment involved in the operation of these facilities. Studying the attacks of this group can help infrastructure entities harden their ICS & SCADA systems from future attackers, foreign or domestic.
END TEARLINE
Final Analyst Comments:
The outage caused by CrowdStrike marks one of the most notable cyber events of this year. It highlights the importance of testing software patches before deploying theme. Deploying to smaller groups instead of globally and staggering the scheduling these rollouts would’ve helped CrowdStrike catch this issue before it became a global incident. With an event such as this, it is crucial to be wary of disinformation and to do your own research into what the best remediation is for your organization. Some issues are out of your control, but contingencies can always help. The sanctions against CARR members underline the importance of cybersecurity in organizations that handle national infrastructure. The research and crime groups described in this report also show a disturbing trend in the accelerated sophistication of attack mechanisms. Having robust threat intelligence systems can help your organization monitor stay ahead of trends affecting your infrastructure. It is also important for vendors to conduct their own security research to ensure they beat attackers to the punch when it comes to vulnerabilities.
Analyst: ResidentGood
END REPORT
If you are interested in anything Cybersecurity, come check out our discord
Sources:
- https://thehackernews.com/2024/07/faulty-crowdstrike-update-crashes.html?m=1
- https://www.crowdstrike.com/blog/to-our-customers-and-partners/
- https://thehackernews.com/2024/07/cybercriminals-exploit-crowdstrike.html?m=1
- https://www.cyberark.com/resources/threat-research-blog/identity-crisis-the-curious-caseof-a-delinea-local-privilege-escalation-vulnerability
- https://arstechnica.com/security/2024/07/code-sneaked-into-fake-aws-downloadedhundreds-of-times-backdoored-dev-devices/
- https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-saesa-afw-bGG2UsjH#:~:text=Summary,on the underlying operating system
- https://www.theregister.com/2024/07/16/rite_aid_says_22_million/
- https://arstechnica.com/security/2024/07/rite-aid-says-breach-exposes-sensitive-details-of2-2-million-customers/
- https://www.bleepingcomputer.com/news/security/sexi-ransomware-rebrands-to-apt-inccontinues-vmware-esxi-attacks/?ref=blog.netmanageit.com
- https://www.sentinelone.com/labs/fin7-reboot-cybercrime-gang-enhances-ops-with-newedr-bypasses-and-automated-attacks/
- https://cloud.google.com/blog/topics/threat-intelligence/apt41-arisen-from-dust
- https://home.treasury.gov/news/press-releases/jy2473



