Intelphreak - 11:30Z September 18th, 2024
TfL Cyberattack Updates, Cloudflare Outage Leaves Some Websites Inaccessible, Chinese Aerospace Firm Employee Charged for Phishing Aerospace/Military Entities, TDSSKiller Used to Disable EDRs & Kawasaki Motors Europe Leak, Iran Tries to Hack Iraq, Port of Seattle Attack, New Oracle WebLogic Malware

Precedence: Routine
BLUF: Multiple Developments in the Transport for London Cyberattack, Mysterious Cloudflare Outage Leaves Popular Websites Inaccessible, USDOJ Charges Chinese Aerospace Firm Employee for Spear-phishing Aerospace & Military Entities, RansomHub Ransomware Gang Used TDSSKiller to Disable EDRs & Leaks 487GB of Kawasaki Motors’ Data, Iranian APT Targets Iraqi Government with Custom Backdoors, Rhysida Auctions Stolen Port of Seattle Data, New Malware Targets Oracle WebLogic Servers
BEGIN TEARLINE
[Major Incident] Transport for London Cyberattack Investigation
Transport for London (TfL), a government body that handles mass transit in London, is releasing new details on their investigation into the September 1st cyberattack that they state has minimally impacted their operations1. Their staff was facing disruptions related to servicing customers. They have recently confirmed that the personal data of approximately 5,000 customers is at risk of breach2. This data includes banking details. Applications for new photocards, the ability to issue refunds, and live arrival information have been temporarily suspended as TfL responds to the incident. They are having their staff of around 30,000 come into the office to reset passwords, prioritizing more key members4.
AC: These disruptions are mainly due to remedial steps they took to protect their systems including taking some systems offline. TfL stated they will contact customers whose information may be affected. The National Crime Agency has apprehended a 17-year-old male for suspected connection to the incident, citing infractions under the “Computer Misuse Act.” The agency & the National Cyber Security Centre are working with TfL to investigate the event3. Anyone who has been a customer of TfL should monitor their online accounts & communications for suspicious activity.
[Major Incident] Rolling Cloudflare Outage
Cloudflare experienced a rolling outage with its web services that affected organizations worldwide5. Their website indicated maintenance in regions of the United States & Singapore, but nothing was posted about the outage itself. The outage seems to be region-specific as some website visitors are still able to access the sites affected.
AC: There has been very little information so far surrounding this event. Downdetector showed increasing reports from customers who were unable to access websites that used Cloudflare. Notable websites such as NodeJS.org have been affected. Some users on X (Twitter) have been able to access affected websites via IPv6 instead of IPv4.
[National Security] Chinese National Spear-Phished NASA & US Military
The US Department of Justice has levied charges against Song Wu, a Chinese national who worked for the Aviation Industry Corporation of China6. The complaint states Wu created fake emails for the purpose of spear-phishing employees of NASA, the FAA, the US Air Force, the US Navy, and the US Army. The phishing emails masqueraded as fellow employees asking for the source code of restricted aerospace engineering software.
AC: The individual in question is not in custody. Wu has been charged with 14 counts each of wire fraud & aggravated identity theft7. Each wire fraud charge carries a maximum 20-year prison sentence, and Wu faces an additional 2-year sentence if convicted of identity theft. The company he worked for while carrying out the campaign is state-sponsored and manufactures military as well as civilian aircraft.
[Global Security] Iran-Sponsored APT34 Targets Iraqi Government with Malware
APT34 aka “OilRig” has recently carried out new cyber-attacks against several government organizations in Iraq including the Prime Minister’s Office & the Ministry of Foreign Affairs8. The threat actor has been linked to the Iranian Ministry of Intelligence & Security. The newest attacks involve distributing new malware to execute PowerShell code and exfiltrate data. Unique command-and-control(C2) mechanisms were employed including custom DNS tunneling & tailored email C2 channels. The tactics, techniques, and procedures (TTPs) used in the attacks linked them back to OilRig.
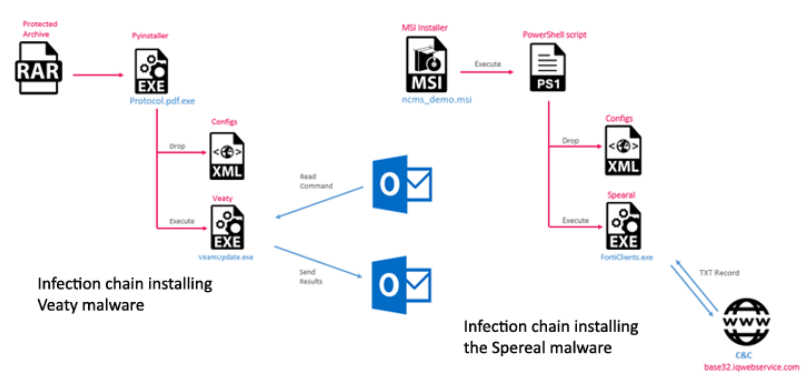
AC: The Spearal malware used in this attack is a .NET backdoor that encodes data in a modified base32 format tucked away in the subdomains of DNS queries to transmit back to the C2 server. The Veaty malware used in this campaign uses compromised Iraqi government emails to download files from C2 channels and execute commands. Check Point’s investigation also uncovered an SSH tunneling backdoor and an HTTP-based backdoor. This targeting of critical Iraqi IT infrastructure is likely to continue evolving. View Check Point’s report for a list of IOCs and protections.
[Cybercrime] RansomHub Ransomware Gang Using TDSSKiller to Disable EDRs & Kawasaki Motors Leak
Ransomware group RansomHub appears to have added TDSSKiller & LaZagne to their TTPs9. TDSSKiller is a legitimate tool authored by Kaspersky Labs for removing rootkits. Researchers from Malwarebytes have observed the group using this tool with the -dcsvc flag to disable Endpoint Detection & Response (EDR) systems. The researchers also cited the threat actor using LaZagne credential harvester. Following a failed extortion attempt targeting Kawasaki Motors Europe, RansomHub has published 487GB of exfiltrated data on their Tor site10.
AC: Malwarebytes has published a list of IoCs to help defend against these attacks. They recommend properly segmenting networks to prevent lateral movement between systems. They also recommend restricting vulnerable drivers such as TDSSKiller. Organizations can allow legitimate use by restricting certain behavior patterns (like using the -dcsvc flag). Kawasaki Motors Europe has informed its clients that they were able to investigate the attack and recover 90% of server functionality.
[Cybercrime] Rhysida Ransomware Gang Auctions Data Stolen from Port of Seattle
The Port of Seattle was hit with an extortion attempt from a threat actor known as “Rhysida11.” The group claims to have stolen terabytes of data from the organization that manages seaports & airports in Seattle, Washington. The group has posted online saying they will auction the data off for 100 Bitcoins. The stolen information includes social security numbers, names, basic biometric data, and even scanned passport copies. The Port of Seattle claims it was able to stop the attack swiftly, and no new malicious activity has occurred since then.
AC: There are conflicting reports on the actual outcome of the extortion attempt. The Port of Seattle has stated publicly that they did not offer to pay the 100 Bitcoin ransom, and they are preparing for the data to be posted online. Rhysida responded by posting an alleged email from the Port of Seattle offering $750,000 for the data. The organization claimed it stopped the attack before everything was encrypted, as in the process of bringing services back online in the safest way possible. The threat actor claims it also obtained employee credentials during the attack. Some operations were affected by the attack & its response. This event marks a growing trend of ransomware groups turning to private auctions for stolen data, rather than solely relying on the threat of leaks.
[Cybercrime] New Malware "Hadooken" Used to Attack Oracle WebLogic Servers
Researchers at Aqua Security have reported a new malware deemed “Hadooken” that is being deployed against Oracle WebLogic servers used to deploy & manage distributed applications12. These servers are valuable targets for the threat actors due to their popularity in critical enterprise environments. Once the hacker compromises a system, they load a Python script that distributes Hadooken, and a shell script that does the same but also allows for lateral movement & further reconnaissance. Once executed, Hadooken itself installs a cryptocurrency miner and the Tsunami Linux DDoS botnet malware. Finally, logs are wiped, and evasion tactics are employed to disguise the malicious activity behind legitimate processes. Researchers also uncovered possible links to ransomware software, hinting at another possible tactic within the campaign.

AC: Aqua Security has made an astounding discovery. Their full report can be found here and contains further information for securing against these threats. These targets are valuable to attackers because Oracle WebLogic servers, and Linux servers in general tend to have access to vast resources. This makes it perfect for adding fuel to a DDoS botnet, and for mining cryptocurrency. These WebLogic servers also tend to be employed by large corporations & organizations that have valuable data for a ransomware attack. The largely integrated nature of corporate information systems also makes it a worthy target for lateral movement.
END TEARLINE
Final Analyst Comments:
Rising geopolitical tensions and shrewd threat actors have made for another interesting week in cybersecurity. With the TfL, Port of Seattle, and Iran-Iraq stories we have examples of the immense target on the back of all public sector organizations, regardless of size or function. A lot of the attacks in this report boil down to social engineering and compromised credentials. Having relevant & tailored SATE training can help protect information systems from one of the most ubiquitous weaknesses: email inboxes. Having robust processes to allow for the triaging of malicious communications is especially valuable for organizations with sensitive operations. Finally, another lesson we can learn from these stories is the changing state of cyber extortion. Criminal groups have turned ransomware into a billion-dollar business, and the market surrounding stolen data is advancing. If your company’s data is breached, the attacker may not just seek a ransom from you but the highest bidder. The rise of Ransomware-as-a-Service has made it easier for attackers to modularize their campaigns & share technology. Defenders must learn to do the same for their defenses. The silver lining is the security research community continues to grow as the threats do.
Analyst: ResidentGood
END REPORT
If you are interested in anything Cybersecurity, come check out our Discord
Sources:
- https://www.bleepingcomputer.com/news/security/transport-for-london-confirms-customer-data-stolen-in-cyberattack/
- https://www.theregister.com/2024/09/12/transport_for_londons_cyber_attack/
- https://www.bbc.com/news/articles/c4gqg2elkj4o
- https://www.cyberdaily.au/security/11115-tfl-issues-in-person-password-resets-for-its-30k-staff
- https://www.bleepingcomputer.com/news/technology/cloudflare-outage-cuts-off-access-to-websites-in-some-regions/
- https://www.securityweek.com/doj-chinese-man-used-spear-phishing-to-obtain-software-from-nasa-military/
- https://securityaffairs.com/168514/cyber-crime/chinese-man-spear-phishing-nasa-us-government.html
- https://thehackernews.com/2024/09/iranian-cyber-group-oilrig-targets.html
- https://securityaffairs.com/168296/malware/ransomhub-ransomware-tdskiller-disable-edr.html
- https://www.securityweek.com/ransomware-group-leaks-data-allegedly-stolen-from-kawasaki-motors/
- https://www.theregister.com/2024/09/17/rhysida_port_of_seattle/
- https://www.bleepingcomputer.com/news/security/new-linux-malware-hadooken-targets-oracle-weblogic-servers/



