Intelphreak - 10:00Z September 4th, 2024
IT Outages in Netherlands, PoorTry Windows Driver Evolves, Iran-Sponsored Threat Actor Engages in Intelligence Operations on US & UAE targets, FlyCASS Vulnerability Risks Security Bypass, NK Threat Actors Exploit Chrome Zero-Day, GitHub Comments Distributing Malware, Cicada3301 Targets ESXi Systems

Precedence: Routine
BLUF: Widespread Outages in Netherlands Linked to Network Disruption at Ministry of Defense, PoorTry Windows Driver Used to Wipe EDR Files by Ransomware Groups, Iran-Sponsored Threat Actor Engages in Intelligence Operations Including the Use of a Multi-Stage Backdoor Malware on US & UAE targets, Researchers Find FlyCASS Vulnerability That Allows Attackers to Potentially Bypass Airport Security Screening, North Korean Threat Actors Exploit Chromium Zero-Day to Deploy Malware, Thousands of GitHub Comments Distribute Lumma Stealer Malware, New Cicada3301 Ransomware Targets ESXi Systems
BEGIN TEARLINE
[Major Incident] Ministry of Defense Network Issue Causes Widespread Disruptions in the Netherlands
A network outage in the Netherlands’ Ministry of Defense has led to widespread disruptions in IT systems across the Netherlands1. Flights were grounded, consumer telephony was affected, and emergency services were experiencing malfunctions. The cause is still being investigated, not all of these events have been linked to the Ministry of Defense issue with certainty.
AC: The main emergency phone line (112) was not affected by this event2. Most of the outages are being gradually fixed and businesses are continuing normal operations in the Netherlands. This event has not been attributed to a cyber-attack. This event is another in a series of widespread IT outages this year.
[National Security] Iran-Sponsored APT “Peach Sandstorm” Deploys Multi-Stage Windows Backdoor
From April to July of this year, Microsoft discovered an APT linked to the Iranian Revolutionary Guard Corps (“Peach Sandstorm”) utilizing a multi-stage backdoor for Windows systems (“Tickler”) as part of a long-term intelligence gathering operation3. The malware was used to target governmental, energy, communications, and satellite technology organizations in the US & the United Arab Emirates (UAE). This operation also involves password spray attacks where a common list of passwords is used to try to authenticate a plethora of user accounts. This APT has also conducted espionage & social engineering using LinkedIn, and the accounts they were using have been taken down. Peach Sandstorm used compromised Azure tenants and student Azure subscriptions to host command-and-control servers to deploy the Tickler backdoor. Once in the network, the threat actor uses the Server Message Block to move laterally and attempts to install Remote Monitoring & Management tools like AnyDesk. In one instance, Peach Sandstorm used a malicious .zip file to compromise a user and take a snapshot of Active Directory.
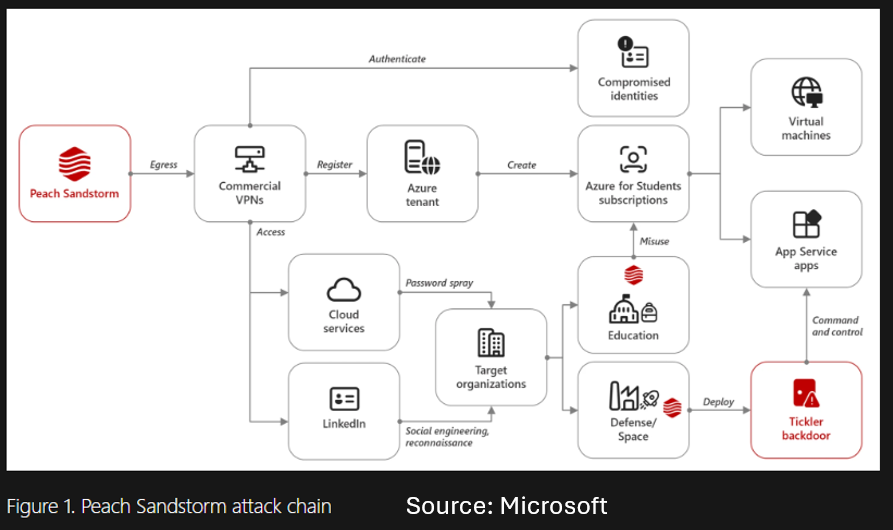
AC: Microsoft has released a very detailed report on this threat group. Any organizations in the targeted sectors & countries should review the report as it contains a thorough list of methods to secure against the APT’s methods. This group is an interesting case study in modern cyber espionage. Iran-sponsored threat activity has been very high this year, and this is one of many groups conducting espionage via information systems. Organizations that fit the target profile of Iranian cyber espionage groups should stay on the pulse of these discoveries.
[Research] Vulnerability in TSA Systems Allows For SQL Injection to Bypass Security Screening
Security researchers Ian Carroll & Sam Curry have discovered a vulnerability in FlyCASS that allows for SQL injection into a database of employees who are allowed to bypass TSA security screening4. The researchers have attempted to responsibly disclose this security gap to both DHS & the TSA with mixed results5. DHS responded to the researchers by acknowledging the critical vulnerability & fixing it after temporarily disconnecting FlyCASS from the Known Crew Member (KCM) & Cockpit Access Security System (CASS) databases. Then DHS stopped answering the researchers’ emails. The TSA on the other hand has released conflicting statements about the vulnerability. Most recently, the TSA press secretary has made a public statement that “no government data or systems were compromised and there are no transportation security impacts related to the activities…” He also stated: “TSA does not solely rely on this database to verify the identity of crewmembers. TSA has procedures in place to verify the identity of crewmembers and only verified crewmembers are permitted access to the secure area in airports. TSA worked with stakeholders to mitigate against any identified cyber vulnerabilities.”
AC: This research is a very critical finding, and the patching of the vulnerability is a vital step in ensuring transportation security. This weakness in the FlyCASS software also allowed users to manipulate other records in the employee databases. There has been no known exploitation of this vulnerability in the wild. After this research was published, another security researcher found that FlyCASS may have suffered from a MedusaLocker ransomware attack earlier this year. Embracing responsible vulnerability disclosure is paramount to securing an information system. It encourages security researchers to help organizations further their security standards, protecting operations before attackers can disrupt them.
[Cybercrime] Ransomware Gangs Use "PoorTry" Windows Driver to Wipe EDR Files
“PoorTry” (also known as “BurntCigar”) is a kernel-mode driver for Windows used by threat actors to bypass/disable Endpoint Detection & Response (EDR) systems6. This malware was made 3 years ago and was first seen evolving in capability in 2023 by Trend Micro. It upgraded from deactivating EDRs to wiping critical files needed to restore EDR integrity. It now allows the deletion of hardcoded lists of files, user-input file names, and user-input file types. Sophos has recently disclosed instances of this new version of the malware being used in a RansomHub attack7. Attackers use multiple versions of the same malware signed with different certificates to evade detection.
AC: This is a remarkable advancement in tactics that makes it harder to defend against these payloads. The new versions of the software make it harder to defend against attackers using it, but it may allow for a higher probability of catching attacks before encryption ensues.
[Cybercrime] North Korean APTs Exploit Chromium Zero-Day to Deploy Rootkits & Other Exploits
Multiple North Korean threat actors, suspected to be a subgroup of “Lazarus Group” have been discovered exploiting a zero-day remote code execution (RCE) vulnerability in Chromium, CVE-2024-79718. The vulnerability is a type confusion in V8’s JavaScript & WebAssembly engine. It allows attackers to remotely execute code in the Chromium renderer sandbox. It is allegedly triggered by users navigating to a malicious web page. The attackers used this RCE access to install the FudModule rootkit and CVE-2024-38106, a Windows sandbox escape exploit9. This gives the attackers administrative & kernel access to the target host systems. The threat actors have been using exploits after patches were issued by vendors like Google and Microsoft.
AC: The threat actors in question have been given many different names including AppleJeus, Labyrinth Chollima, UNC4736, Hidden Cobra, and Nickel Academy. Targets include financial institutions and individuals that work with cryptocurrency, the motive being monetary of course. The group and infrastructure involved have been tied to North Korea’s Reconnaissance General Bureau. Microsoft has issued many recommendations for security against this group. They are installing the latest security updates for browser applications, using Defender SmartScreen when web browsing, hardening Defender for Endpoint configuration, strengthening Defender Antivirus configuration, and using their relevant profiles for Defender Threat Intelligence. View Microsoft’s report for more details on how to secure against these threats.
[Cybercrime] Attackers Use Thousands of GitHub Comments to Distribute Lumma Stealer Malware
A contributor to the teloxide rust library made a post about several comments in their GitHub issues page that masqueraded as solutions but turned out to be the Lumma Stealer malware10. BleepingComputer has discovered thousands of these fake fixes attempting to distribute the payload via GitHub comments. The comments implore users to visit suspicious URLs to download an encrypted archive file. The executable in this payload was found to be a copy of Lumma Stealer, a malware that steals data like credentials and credit cards from popular web browsers. It also can steal important cryptocurrency data from the target. This stolen information is archived and transmitted back to the threat actor.
AC: GitHub has been doing its best to delete these comments as users come across them. There has been no attribution of this attack, but it aligns with Stargazer Goblin’s past activity. Stargazer Goblin used thousands of compromised GitHub accounts to distribute malware that also exfiltrates confidential data. The easiest way to mitigate this attack is to train staff who use GitHub on anti-phishing & anti-social engineering techniques. The simple act of not clicking a suspicious download link on a GitHub comment would prevent the spread of this malware. The suspicious links in question are under the “mediafire.com” & “bit.ly” domains. Users should instead report these comments to GitHub so they can be taken down.
[Cybercrime] Cicada3301 Ransomware Operation Targets VMWare ESXi Systems
Cicada3301 ransomware that previously targeted Windows & Linux systems now has a version that targets VMWare ESXi systems11. This malware is written in rust and shares a shocking number of other similarities to ALPHV ransomware. It is plausible that Cicada3301 is a rebranding of ALPHV, but it is not yet proven. The ransomware can delay its execution, display the real-time progress of encryption, and encrypt ESXi files without shutting down the VM & deleting any snapshots of the VM. The program uses symmetric encryption and creates a ransom note file in the folders containing the encrypted data. It is suspected this variation is an adapted version of the original Windows version of the ransomware.
AC: This ransomware outlines the importance of hardening virtualized systems. Attackers have been adapting to the growing use of hypervisors in corporate environments. Truesec has created a YARA rule to assist in hunting this particular threat actor.
END TEARLINE
Final Analyst Comments:
Several key insights can be gleaned from these events. The Netherlands outages show us the fragile nature of heavily-integrated network infrastructure. Organizations can prepare thorough disaster procedures to continue operations in the case of a network outage as large as this one. The “PoorTry” & Cicada3301 ransomware stories indicate the immense capability of threat actors to adapt to improved security measures. This is why security teams cannot afford to become complacent in their current security strategies. The Peach Sandstorm story shows how advanced cyber espionage has become. Combining traditional attacks like password spraying, with advanced backdoor malware allows APTs to gain persistent access to systems in order to exfiltrate data. Both private and public organizations must harden their systems from the next-level abilities of state-sponsored threats. Robust cyber threat intelligence systems and processes can aid in this regard. The FlyCASS SQL Injection case shows how important it is to validate any user input on a web application, especially when it is connected to such critical databases. It also shows how organizations can leverage the security research community by embracing responsible disclosures. The Chromium exploitation anecdote shows how important it is to keep systems updated. Patches should be applied regularly, especially when they concern such critical vulnerabilities. Finally, the GitHub comments distributing Lumma Stealer outline another instance where Security Awareness Training & Education is vital for both employees and individuals. GitHub tends to have a more tech-savvy audience, and yet some users still clicked on suspicious links.
Analyst: ResidentGood
END REPORT
If you are interested in anything Cybersecurity, come check out our discord
Sources:
- https://apnews.com/article/netherlands-network-breakdown-defense-ministries-airport-cyber-37a5287f3369fe12cad6da1a1a0c4f1e
- https://tweakers.net/nieuws/225878/netwerkstoring-bij-defensie-leidt-tot-problemen-bij-nederlandse-overheden.html
- https://www.microsoft.com/en-us/security/blog/2024/08/28/peach-sandstorm-deploys-new-custom-tickler-malware-in-long-running-intelligence-gathering-operations/
- https://ian.sh/tsa
- https://www.bleepingcomputer.com/news/security/researchers-find-sql-injection-to-bypass-airport-tsa-security-checks/
- https://www.bleepingcomputer.com/news/security/poortry-windows-driver-evolves-into-a-full-featured-edr-wiper/
- https://news.sophos.com/en-us/2024/08/27/burnt-cigar-2/
- https://thehackernews.com/2024/08/north-korean-hackers-deploy-fudmodule.html?m=1
- https://www.microsoft.com/en-us/security/blog/2024/08/30/north-korean-threat-actor-citrine-sleet-exploiting-chromium-zero-day/
- https://www.bleepingcomputer.com/news/security/github-comments-abused-to-push-password-stealing-malware-masked-as-fixes/
- https://securityaffairs.com/167897/cyber-crime/a-new-variant-of-cicada-ransomware-targets-vmware-esxi-systems.html



