TryHackMe Room Writeup: Sakura
This writeup covers the TryHackMe "Sakura" room, featuring an OSINT investigation into a fictitious hacker who attacked the OSINT Dojo. This room is designed to test a diverse range of OSINT techniques, including those related to image, social media, and geolocation intelligence.

Created by SirPicklJohn (Ayden Parsons)

SirPicklJohn's Writeup of OSINT Dojo's Sakura TryHackMe Room
SECTION 1: TIPOFF
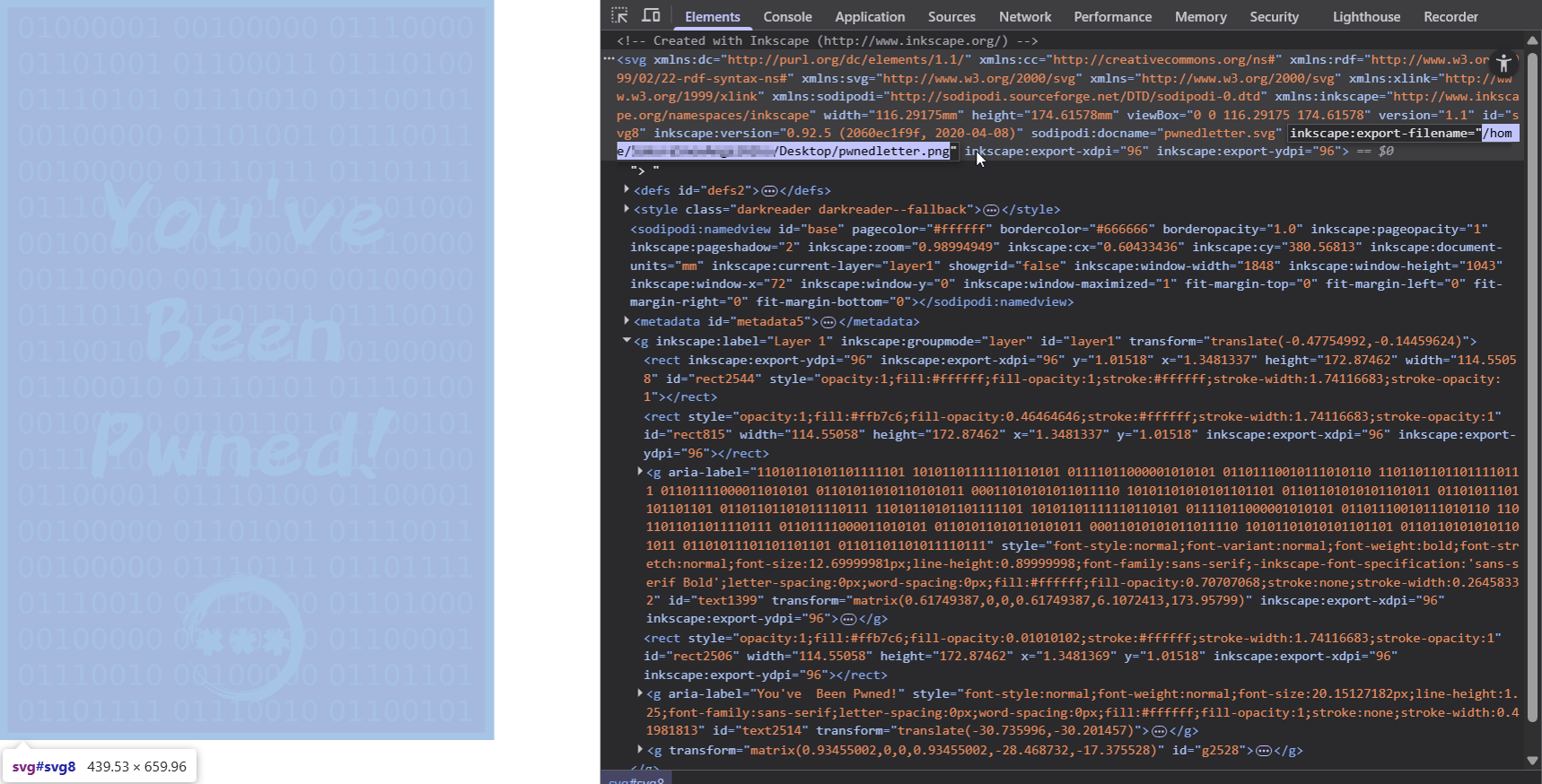
Using the photo initially provided by OSINT Dojo (allegedly left behind by the cybercriminal we are tracking), the username of the attacker can be found in the image's metadata. This can be found by going to the developer tools and reading the contents of the "export-filename" metadata tag (shortcut: CTRL+SHIFT+I).
SECTION 2: RECONNAISSANCE
Simple Google Dorking reveals a lot about the attacker and provides some useful repositories of information to pivot off of, including an Instagram, Reddit, and Github. Several of these hold the attacker's real name.
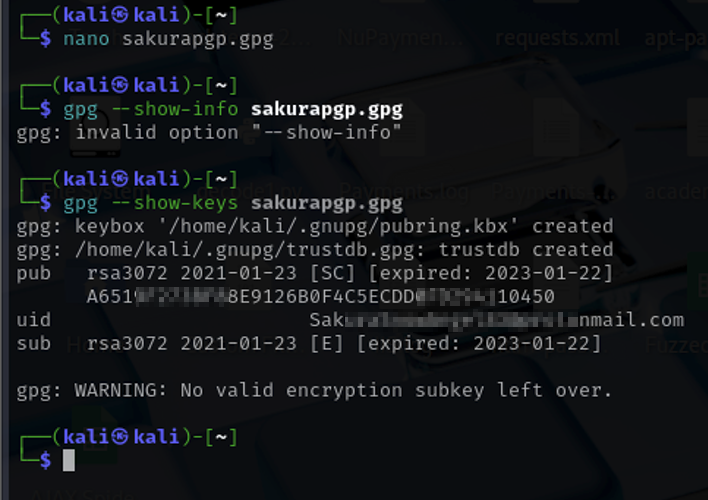
On the Github, you can see a repository called "GPG key". Researching more, you can learn that an email address can be derived from a GPG key's Key ID. This Key ID can be extracted by performing a reverse PGP key lookup.
This forum showed how to extract the Key ID from a keyring, and running the appropriate command both gave me the Key ID and the corresponding email address.
SECTION 3: UNVEIL (Cryptocurrency Questions)
Looking back at the attacker's Github, you can see a variety of cryptocurrency-related repositories that can tell you a few things about their activities:
- Various repositories suggest they could have a wallet for Ethereum, Litecoin, and/or Bitcoin - another repository named "ETH", which has a "miningscript" and the content
stratum://ethwallet.workerid:password@miningpool:portconfirms that the attacker owns a wallet for Ethereum. - Looking at the commit history for the ETH repository, you can see the attacker's uncensored wallet address.
- Looking this wallet up on something like blockchain.com shows information on the wallet, its contents, and all of its historical transactions.
SECTION 4: TAUNT
Looking at a screenshot of the messaged taunt to OSINT Dojo from the attacker, you can see their Twitter/X handle (i.e., username):
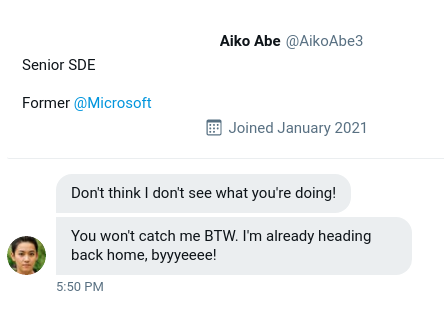
Searching this handle (either on Twitter/X or a search engine) reveals the attacker's account, and seeing the other posts they've made reveals other interesting information that will help us later. One of the attacker's posts connects @AikoAbe3 to their real handle:
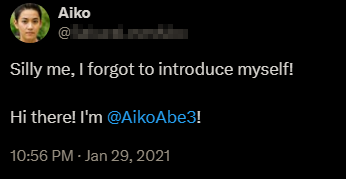
("APs" likely refers to "Access Points" here.)
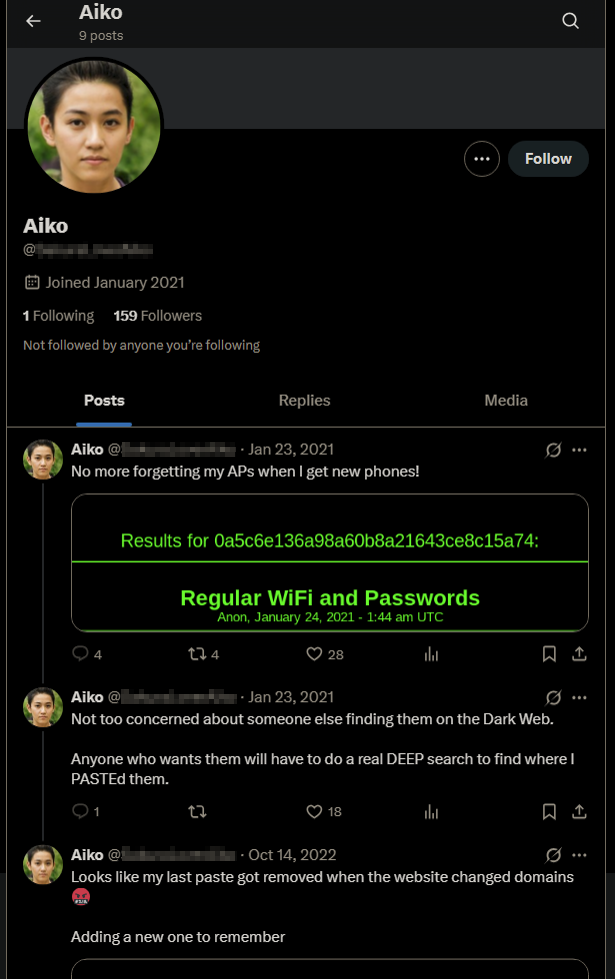
Some quick research on what the hinted term "deep paste" means in relation to the dark web reveals that "DeepPaste" is or was a pastebin site for sharing simple text on the dark web.
Unfortunately, more researching showed that others trying to complete the Sakura room were having trouble with this challenge, and that DeepPaste may not exist anymore (corroborated by the fact most other existing onion links to DeepPaste are old and don't work). What was on the paste were several pairings of access point names (i.e., SSIDs) and passwords, one of which was labelled "Home WiFi" with the name "DK1F-G". (This could be found from other writeups or forum discussions.)
After this, WIGLE.NET (one of the best tools for OSINT investigations involving wireless access points) can be used to identify this access point's geolocation and BSSID. Searching its SSID on WIGLE.NET reveals its BSSID (as well as other information like location):
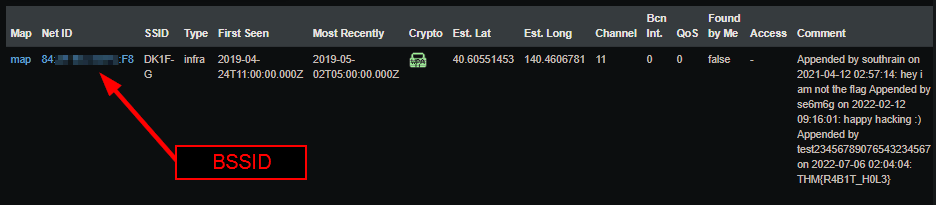
SECTION 5: HOMEBOUND
The following three posts on the attacker's Twitter/X account can be used to find the flags to the next few questions:
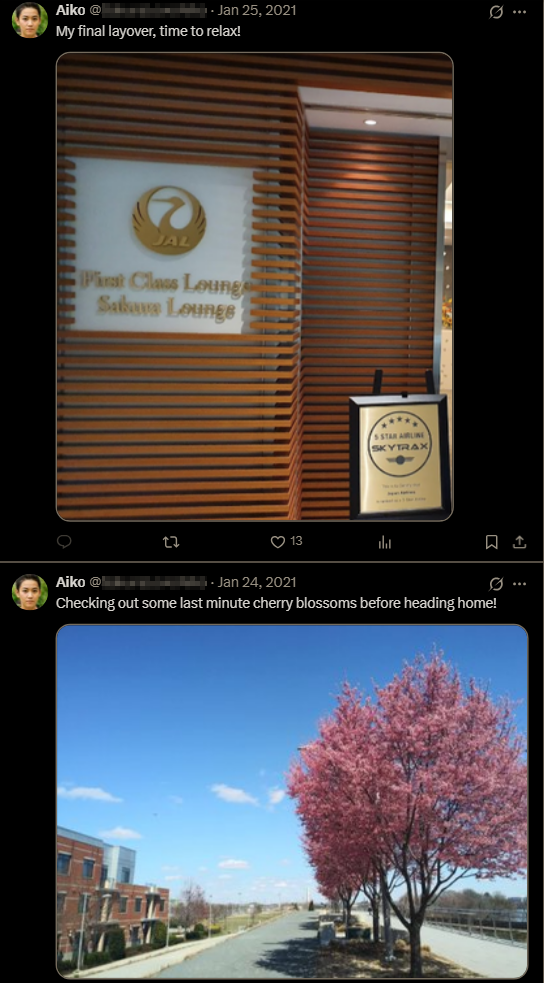
In the post from January 24th, you can zoom in and see the easily-recognizable Washington Monument in the background.

Going to Google Maps and searching the area around the monument shows that the park by the Martin Luther King Jr. and Jefferson memorials have cherry blossom trees as well. The closest public airport to this location is the Ronald Reagan Washington airport, the IANA (three-letter identification) number of which is the flag.
After that, we can search for airports that meet the following criteria to get a list of airports our attacker could have stayed in during their final layover:
- Contains a "Sakura Lounge";
- Is rated as a "5 STAR AIRLINE" by Skytrax (as detailed by the board in the photo);
- Frequently receives flights from the Ronald Reagan Washington Airport; and
- Is located in Japan. (We know the attacker lives in Japan because WIGLE.NET shows the location of the attacker's Home Wifi.)
The two deduced options based on these criteria are the airports located in Narita and Haneda.
I initially tried to compare images posted by travel companies to the features I could see in the hacker's photo, but nothing definitively suggested one airport over the other.
After trying both options, the answer was the IANA code for the airport in Haneda.
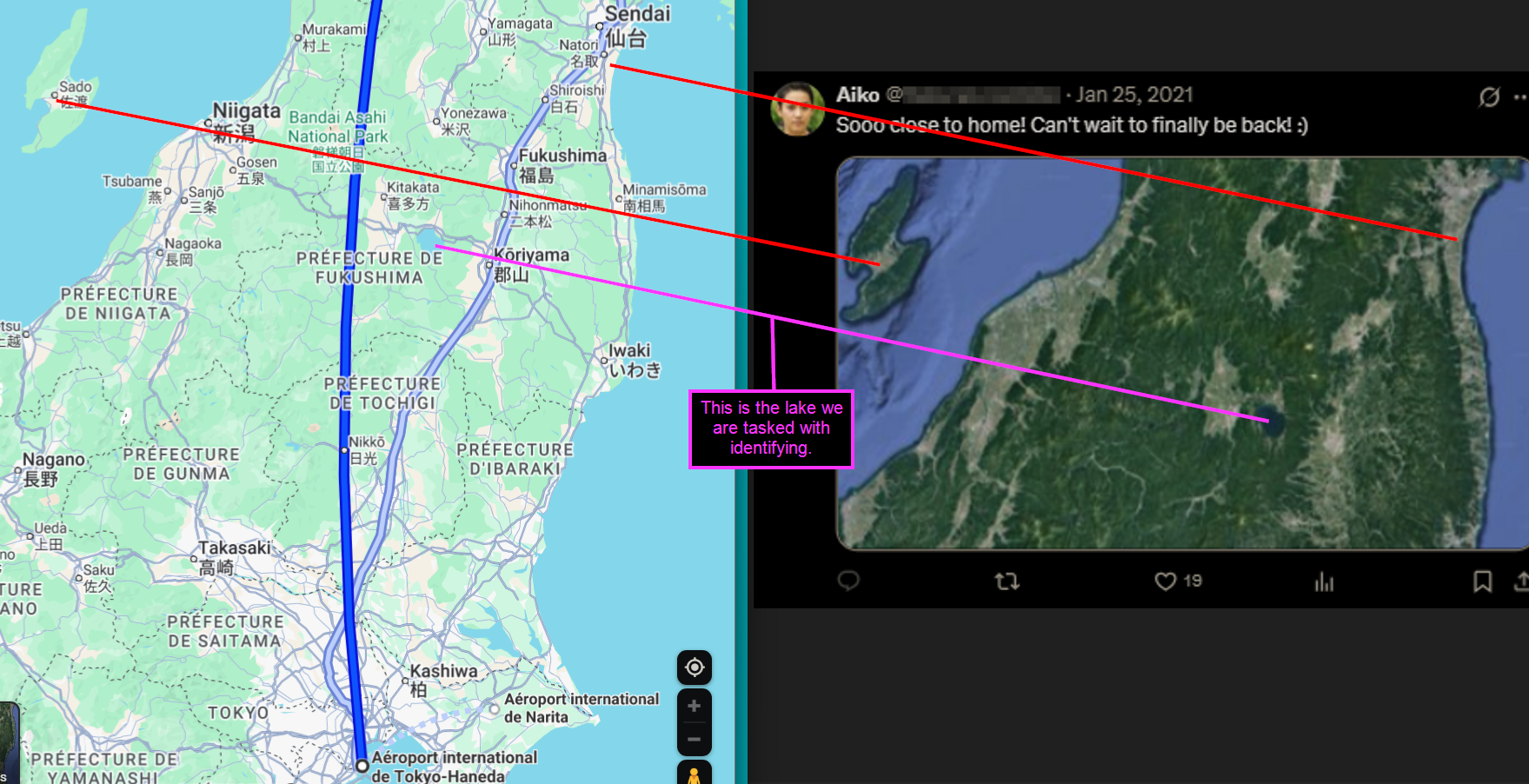
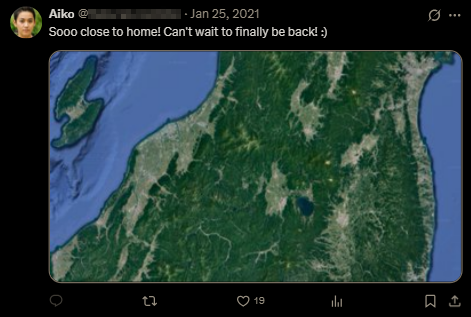
For the second to last flag, the name of the lake can be found by comparing a map of Japan to the image the attacker posted, and tracing a line from Haneda Airport to Aoomori Airport (AOJ - the closest airport to the attacker's home residence) to see what lake is on or next to this line. Very distinguished geographical landmarks like Sado Island in the top left, the curves on both sides of the country, and the lake in the middle of the country make this comparison easy to make on a map.
Thank you for reading!